TrueCrypt: Reports of Its Death Are Greatly Exaggerated
While TrueCrypt’s developers are saying the project is dead, we at Passcovery disagree and are still using TrueCrypt 7.1.
That’s great, but why should you trust our opinion, right?
Our developer went through TrueCrypt with a fine tooth comb while working on the password recovery support module. In the end, he agrees with the software auditors – the source code is transparent and the project uses extremely strong encryption.
Most importantly, he didn’t find any holes or suspicious code in TrueCrypt.
TrueCrypt’s encryption and hash functions are no different than the standards. The random value pool is standard, as well. The application uses good old Windows code – organized, easy-to-read and compact enough to be supported by an individual.
It is theoretically possible that the software has backdoor/bookmark issues that weaken the random process of key generation, but a close study of the source code doesn’t support that theory.
In any case, it would take more that some hidden bugs to damage TrueCrypt’s keys, because the software runs its keys through AES-Twofish-Serpent cascading encryption. It’s hard to imagine how the keys could pass through that kind of gamut and still be susceptible to attack.
Some people have suggested that TrueCrypt could be writing passwords somewhere on the disk, but that is both too obvious and easy to check.
The only possible pitfall would be a memory dump with an open container via a hardware interface like Firewire. That, however, doesn’t have anything to do with TrueCrypt’s reliability.
But are TrueCrypt’s algorithms strong enough?
Most definitely!
The software offers a choice of three algorithms for encryption: AES, Twofish and Serpent. Keys are generated using one of three hash algorithms: RIPEMD-160, SHA-512 or Whirlpool.
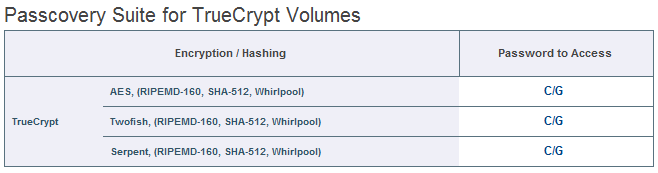
In other words, a classic attack on a TrueCrypt volume would involve putting each potential password through nine pairs of hashing/encryption, growing old while your computer tries to run 1000-2000 hash iterations.
Even lightning fast solutions like our Passcovery Suite would get bogged down on a job like that.
Check out how long it would take on your system using the demo version of our software: it tests your computer’s speed for all supported formats:
So why did they pull the plug on TrueCrypt?
No one knows for sure. So far all we have is rumors.
Maybe the developers got tired of the project and decided to go out with a bang. Or there could be a back story along the lines of Lavabit. Hopefully someone will make a movie about it someday.
For now, we agree with the developers who are currently working to reincarnate TrueCrypt. It’s a sound product that offers reliable encryption.
At the end of the day, that’s good enough for us.