TrueCrypt Password Recovery Using Passcovery Suite Command Line
Like our other programs, Passcovery Suite allows for Command Line Launch and Attack Fine Tuning. The program opens with a graphic interface and all necessary settings and immediately begins a password search.
Professionals successfully use this feature to recover passwords for Microsoft Office, Zip, Rar, Apple iOS back-ups, etc. However, in dealing with TrueCrypt volumes, even professionals are unsure of how to use TrueCrypt-specific parameters from the command line. We have the answer to that in this post.
TrueCrypt Password Recovery Specifics
Offset
Offset is the first TrueCrypt parameter that needs to be set in the Command Line.
Depending on the user needs, TrueCrypt can create different volume types:
- Normal volume
- Hidden volume
- WDE image (whole disk encryption)
- Backup file of an encrypted system disk (ISO-file)
For each volume type, the data necessary for password recovery has a different location. This is the Offset from the beginning of the volume. To learn more about working with TrueCrypt offsets in our Passcovery Suite, click here.
Hash Function and Encryption Algorithms
Hash/encryption pair is the second parameter to be set in the Command Line.
For reliable data protection TrueCrypt offers a choice of:
- 3 hash function algorithms: RIPEMD-160, SHA-512, Whirlpool
- 8 encryption options: AES, Serpent, Twofish, AES-Twofish, AES-Twofish-Serpent, Serpent-AES, Serpent-Twofish-AES, Twofish-Serpent
The Passcovery Suite graphic interface lets you easily set the Offset and select hash / encryption algorithms for password recovery. You can find out how to set these parameters when launching an attack from the Command Line in our step-by-step instruction.
Launching Attack on TrueCrypt from Passcovery Suite Command-Line
Step 1. Open the TrueCrypt volume you need in Passcovery Suite, open the task wizard and press «Next». This will bring you to the attack parameter settings for TrueCrypt:
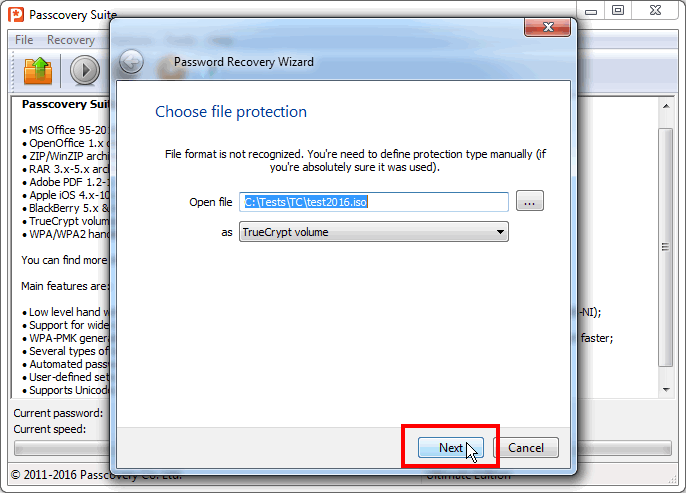
Step 2. Set the volume type (set offset) and checkmark only the hash / encryption algorithms you need:
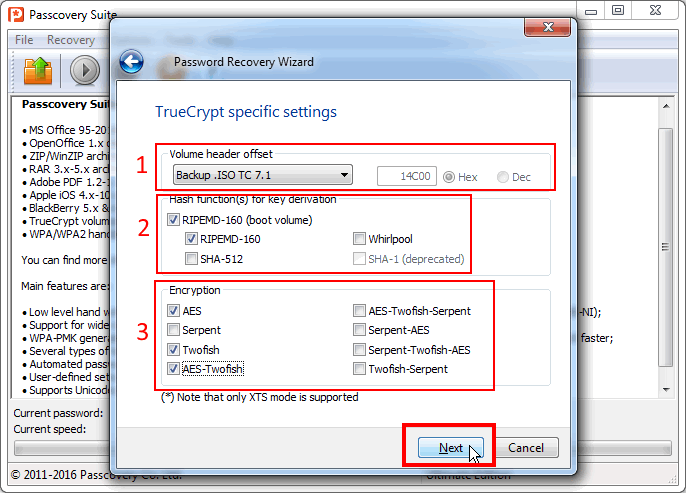
IMPORTANT: As a general rule for recovery of strong passwords, limit the search range as much as possible, always disable the checks known to be unnecessary. Avoiding unnecessary checks will shorten the search time.
Step 3. Set the minimum check range: brute force, numbers, 1 symbol:
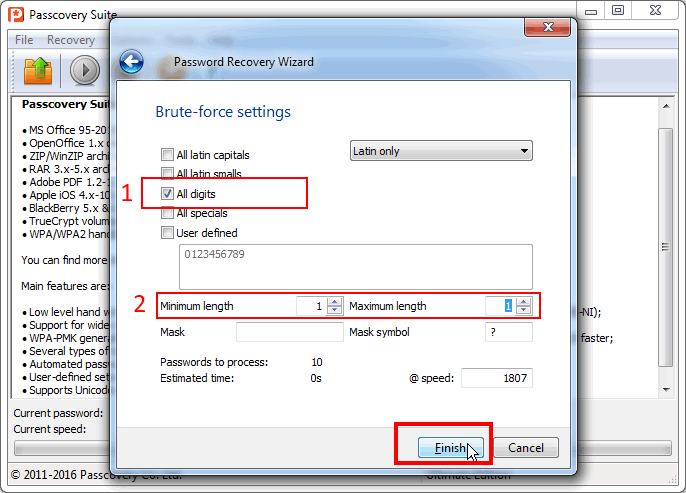
Launch the attack. The sooner it finishes, the better.
Step 4. As soon as Passcovery Suite stops the search and reports that the attack for the given range was successfully completed, press «Start» again:
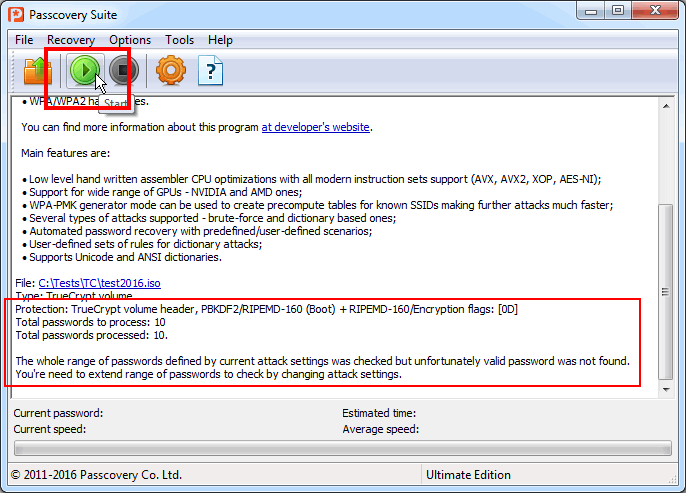
Step 5. In the newly opened Task Wizard window, press «Extract data required for attack…» and save the received .bin file:
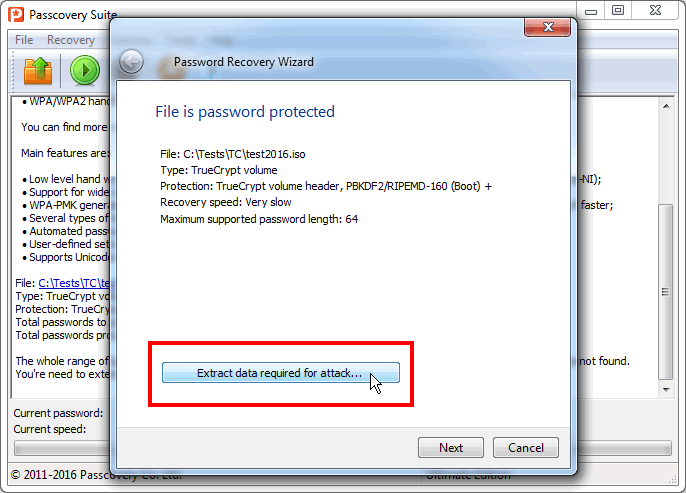
Apart from the data from the TrueCrypt volume necessary for password recovery, the file contains the information on the selected volume type and hash / encryption algorithms.
This file can be copied to other computers to be attacked there and the original TrueCrypt volume is not needed for this. The password will be found without it since all necessary data is in .bin file.
Step 6. Configure the attack launch command as described in this help file. Remember to specify the file to be attacked by search range, script, program parameters; remember, it is the .bin file that you saved earlier.
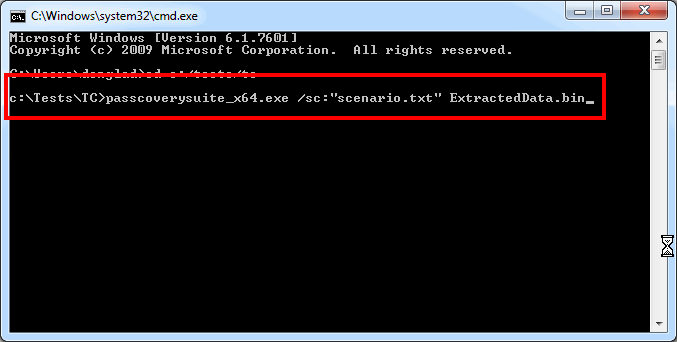
Press «Enter» to start password brute-force search.
Passcovery Suite Scripts
After launch, the Passcovery Suite does an exhaustive search through all combinations within the ranges set by the parameters. For Command Line launch, the search algorithm feature is defined in the script file.
The Script file is not as obvious to work with as the graphic interface, but on the upside it is more flexible and powerful. The script can specify an unlimited chain of prioritized checks to be performed sequentially by the program. You cannot get this flexibility with the graphic interface.
For example, you can start by checking numbers-only passwords of up to 6 characters, then go through the first dictionary, then check lower-case letters-only passwords up to zzzz, etc. Here’s an example of such a script for the Passcovery Suite:
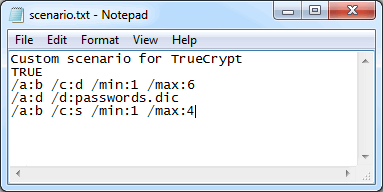
Once launched, the program will sequentially check all ranges described in the scenario. It’s unbelievably convenient!
Learn more about script macros in Passcovery Suite help.
Passcovery Suite 3.8
for Microsoft Office/OpenOffice/LibreOffice, Adobe PDF, Zip/WinZip, Rar/WinRar, TrueCrypt, Apple iOS, BlackBerry OS, WPA/WPA2 handshakes
Download Free Demo