How to Remove Password from Archive & Recover Lost RAR/ZIP Passwords
One of those frequent questions. It constantly arises here and there, in different contexts. So the answer depends on the context and the following:
- What type of archive is it: Zip or RAR?
- Is the password known or has it been lost?
- If the password is lost, what is the easiest way to find it?
In this article I am going to tell you (and showcase) how to most effectively handle password-protected archives and how to find lost passwords quickly (as can be in the case of strong protection).
Let's get started.
Opening a Password-Protected Archive
The principles of protection in modern archives are the same: they all use well-proven and established strong password hashing and data encryption algorithms. The contents of an archive are packed, the password is hashed into a key of sufficient length which is then used to encrypt the archive. Opening and decrypting a password-protected archive occur in reverse order, i.e. you enter the password, the archiver computes the key from it, then decrypts the container and unpacks your files. It's simple!
RAR archive with a password
Start WinRAR archiver, select and open your passworded archive with it. When you initiate extraction of the archive's content, the program will prompt you to enter the password:
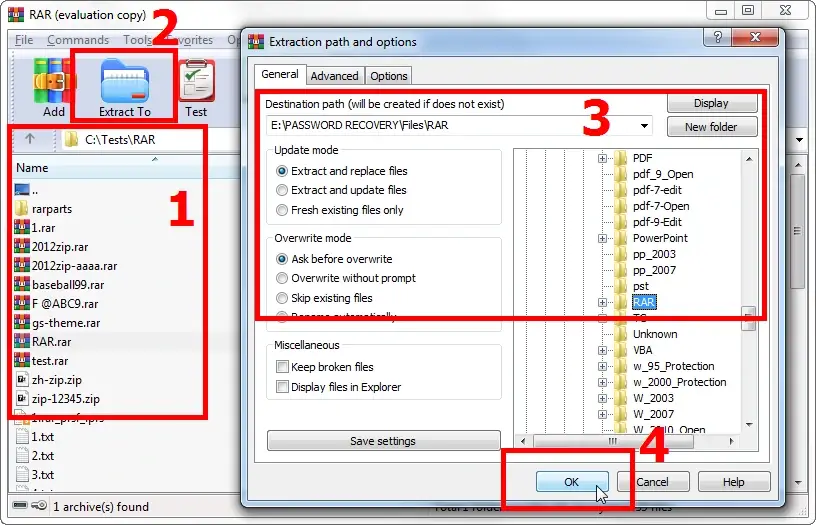
Enter the password and get access to your archived data:
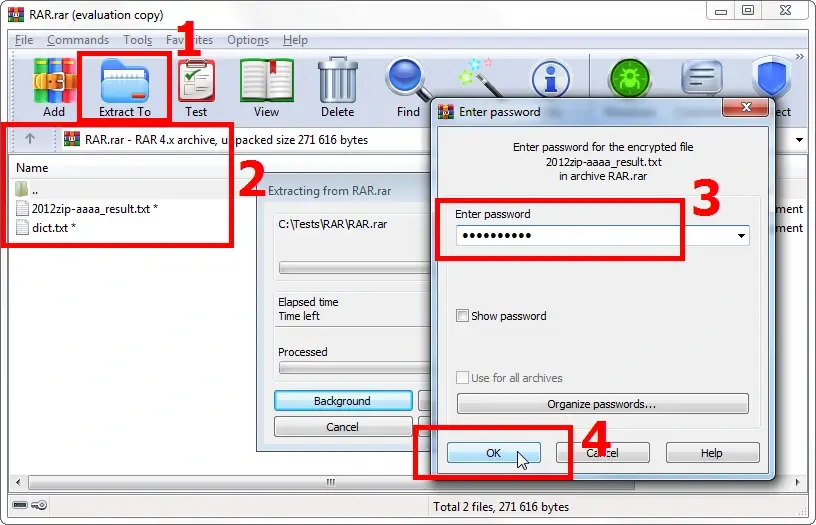
Now you can proceed to work with the content of the archive as usual. When you close the archiver (or the archive file), WinRAR will encrypt the data again and the next time you open the file, you will need to enter the password again.
Zip archive with a password
All that works the same way for Zip archives as well.
Start, for example, 7-Zip archiver. Just like its commercial alternative WinZip, 7-Zip enables you to create archives with classic encryption (aka ZipCrypto encryption method) or more secure archives with AES-256 encryption. use 7-Zip to locate the folder with your archive and double-click on it. This will open the archive. Start extracting your data from the archive or click on the file just like in the Explorer. The program will prompt you to enter the password:
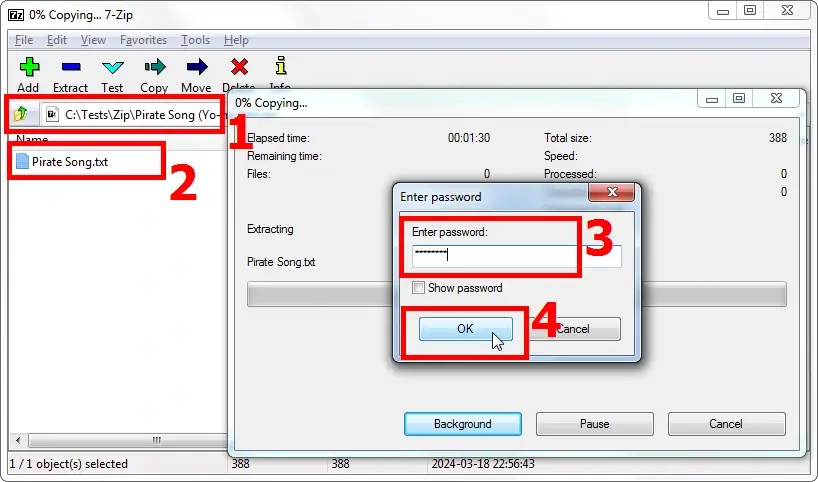
Once you have entered the password, the archiver will unpack, and you will be able to work with your data:
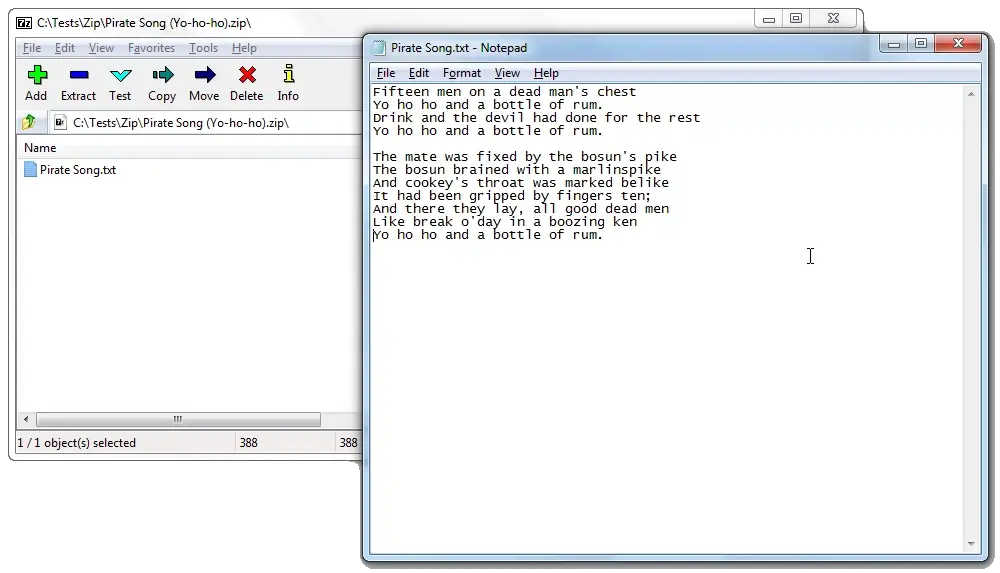
Removing a Password from an Archive
If password protection is no longer needed, it is better to remove the password to avoid its loss or other potential issues.
But here's the thing. One does not simply remove a password from an archive. 😜

To remove the password from an archive, you can only create a new archive, a copy of the one with the password only without such password protection. In other words, you will need to open the passworded archive (as shown above), extract its contents, and then create a new archive.
Here's how you can do it.
Removing the password from a RAR archive
Select the files or the folder that you have extracted from your password-protected archive.
You don't have to select all of them at once. You can start with any of them so you can add the rest of the files to the archive later.
Click the «Add» button. This will initiate the creation of a new archive (or adding files to an existing archive).
In the pop-up window specify the parameters for the new archive: destination folder, name, format, compression methods, etc. Needless to remind you, you don't need to set a password this time, right? 😉
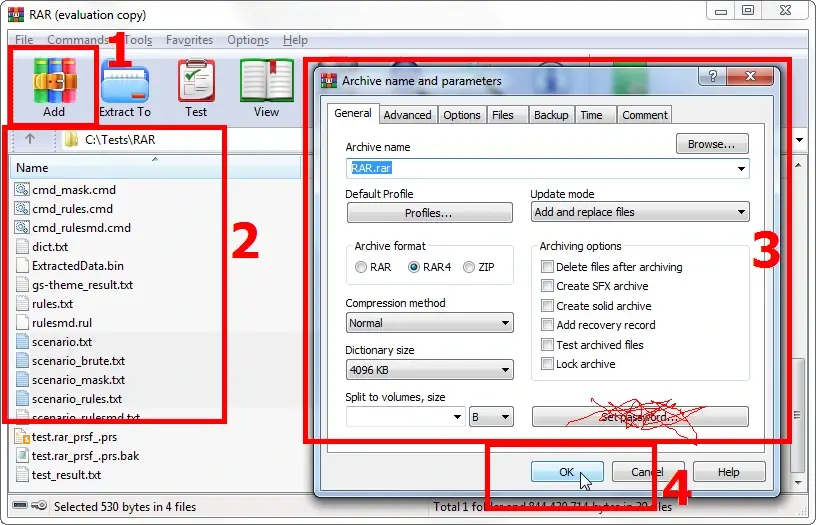
If you want to add files to an existing archive, just select it by clicking on the «Browse…» button.
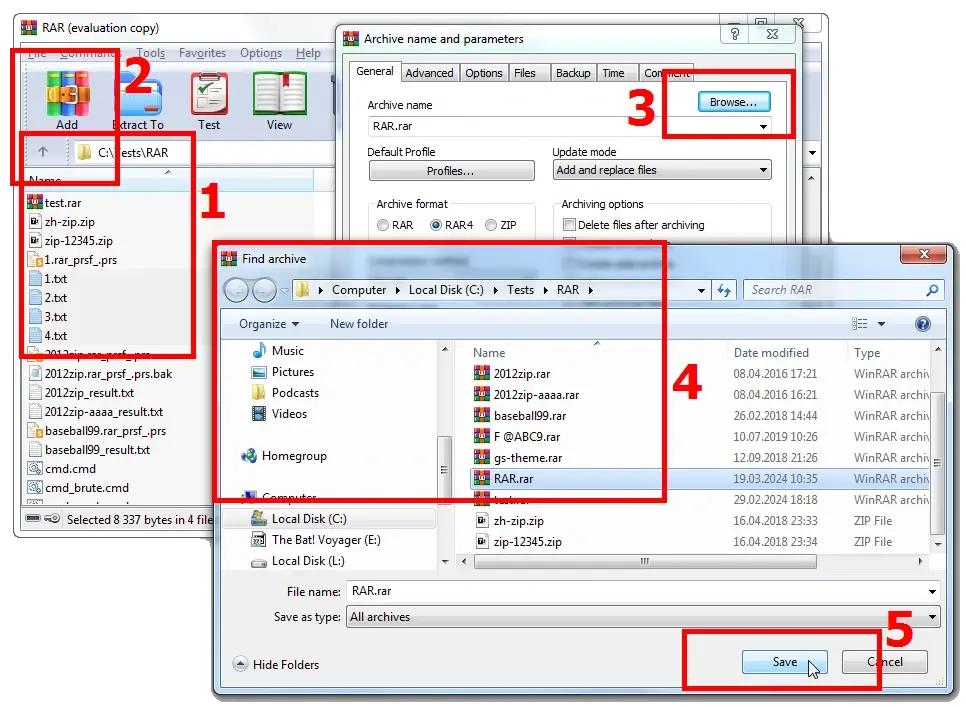
That's about it: click the «ОК» button, and the archiver will create an archive without a password, containing the files extracted from the original password-protected archive. Now you can forget about the password. 😜
Removing a password from a Zip archive
Once again, I suggest using 7-Zip to handle Zip archives. It retains the same sequence of removing a password from a Zip archive. First, unpack the passworded archive and then repack it into a new archive without a password.
Similar interface and exactly the same logic 😉
Select the extracted files you need and click the «Add» button.
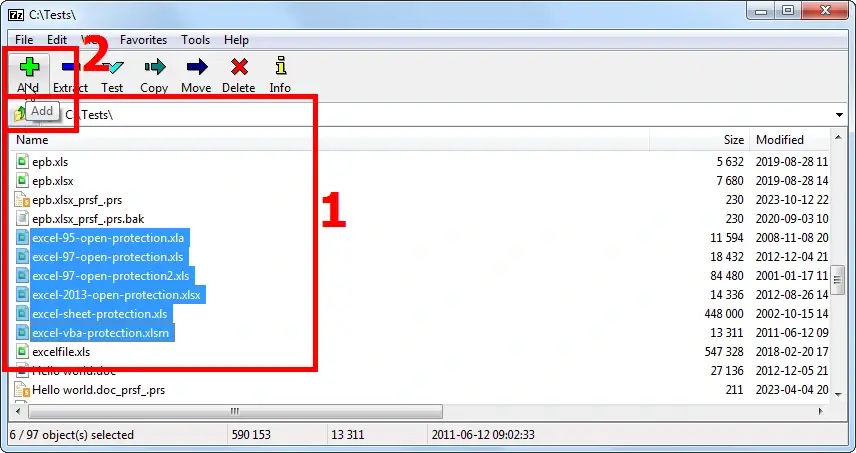
Specify the archiving parameters (note that the options are mostly the same as in WinRAR).
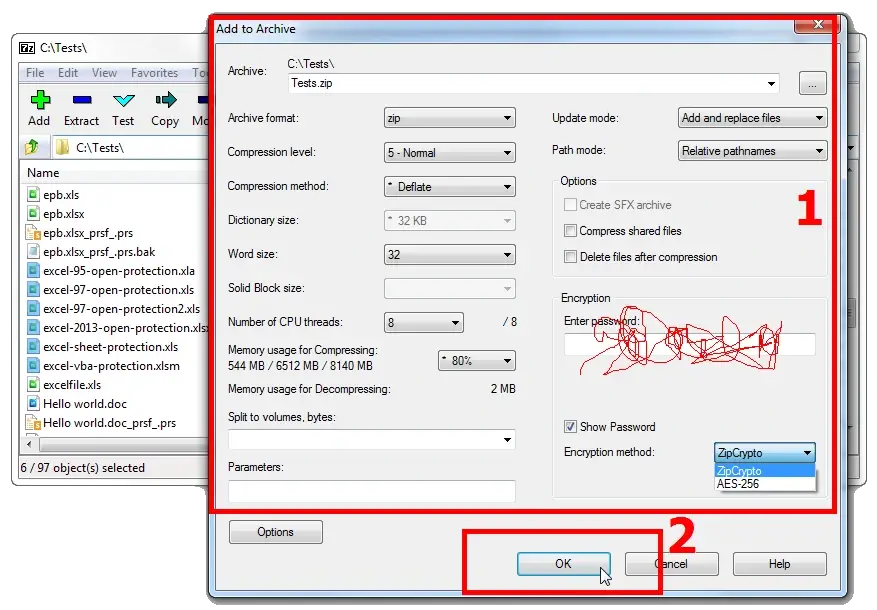
Just Click «ОК» and there you have it – your unlocked Zip archive.
How to Unlock an Archive If the Password is Lost
Well, first, it turned out quite easy to open a password-protected archive and remove the password from it. Everything is intuitively clear and simple.
Admittedly, it's not as simple when the password is lost. 😉
Archivers use impeccably reliable and secure algorithms to protect and encrypt data. These time-proven algorithms have been tested by many. The highly complicated process of generating encryption keys leaves no 'back doors' to use.
When the password for the archive is lost, the only way to regain access to data is to recover the password by trying all possible combinations of characters. This method is known as a brute force attack.
Next.
The number of combinations that need to be tested depends on the password length and the sets of characters used to generate those passwords (i.g. uppercase letters, lowercase letters, numbers, special characters). It can be calculated by the formula:
Number of combinations = number of characters password length
Here are a few examples:
1. A password with a length of 6 characters, consisting only of digits. The total number of combinations to test is: 10 (number of digits from 0 to 9) 6 (password length) = 1 000 000
2. A password with a length of 6 characters, consisting of digits and lowercase Latin letters. In this case, the number of combinations to test is calculated as follows: (26+10) 6 = 2 176 782 336
3. A password with a length of 6 characters, where nothing is known about it, and the entire set of characters has to be tested i.e. 26 (lowercase letters) + 26 (uppercase letters) + 10 (digits) + 33 (special characters). The problem to solve becomes significantly more complex: (52+10+33) 6 = 735 091 890 625
Oopsy-daisy! Suddenly it is not that simple anymore. The testing process will definitely take some time… 😁
To enjoy efficient recovery of passwords to your archives you will need a program that can do the following:
1. iterate through passwords at the maximum processing speed of your computer
2. cut off a priori futile password variations
Let me introduce a couple of software solutions by Passcovery: Accent RAR Password Recovery for RAR archives and Accent ZIP Password Recovery for Zip archives.
Here's what makes each one an excellent choice:
1. Both programs are optimized for operation with various processor families which ensures invariably high speed of password recovery
2. The programs support GPU acceleration on both NVIDIA, AMD and Intel graphics cards (though there may be some limitations 1, 2)
3. They offer three types of password attacks to choose from:
- Brute force attack
- Brute force attack with extended mask
- Dictionary attack
4. The programs provide advanced search customization options to manipulate the range of possible hits:
- Extended (positional) mask to use with the brute force attack
- Combining and mutating dictionaries option to use with the dictionary attack
5. These programs allow you to configure and run diverse attack scenarios with varying levels of complexity
In short, these programs have got all it takes to successfully recover lost passwords. 👍 – ★★★★★
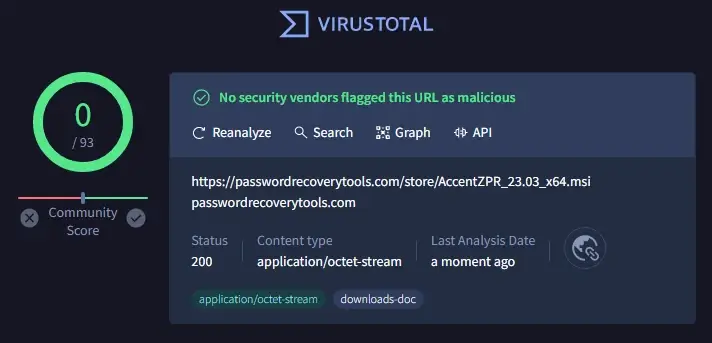
The installation packages are compatible with Windows, signed by Passcovery, and absolutely free malware (VirusTotal – 0/93).
You can download, install and start using the programs right away. Now let me guide you through the process of recovering a password for an archive.
| Accent RAR Password Recovery for passwords to RAR archives |
||
| Accent ZIP Password Recovery for passwords to Zip archives with classic and AES-256 encryption |
In my example, I will work with a Zip archive using Accent ZIP Password Recovery. All Passcovery programs have a unified interface, with the only difference being the supported formats. So lost RAR passwords can be recovered in the exactly same way.
1. Start the program and open your password-protected archive. Enjoy the usual navigation in Windows i.e. the menu, taskbar icon, or hotkeys («Ctrl+O»):
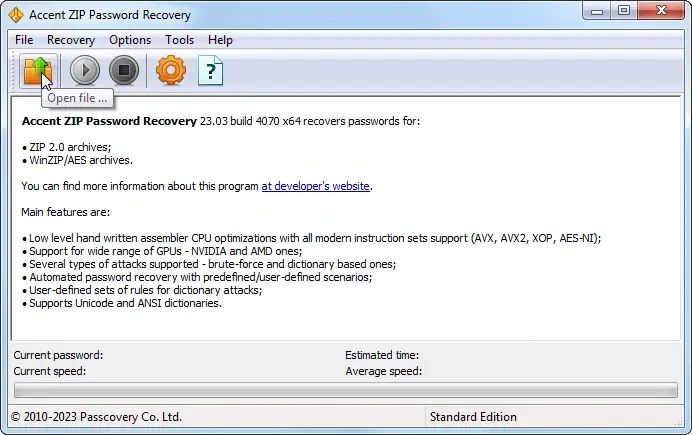
2. At this stage the program will define the type of protection enabled and give a rough estimate of the time required to complete a brute force attack:
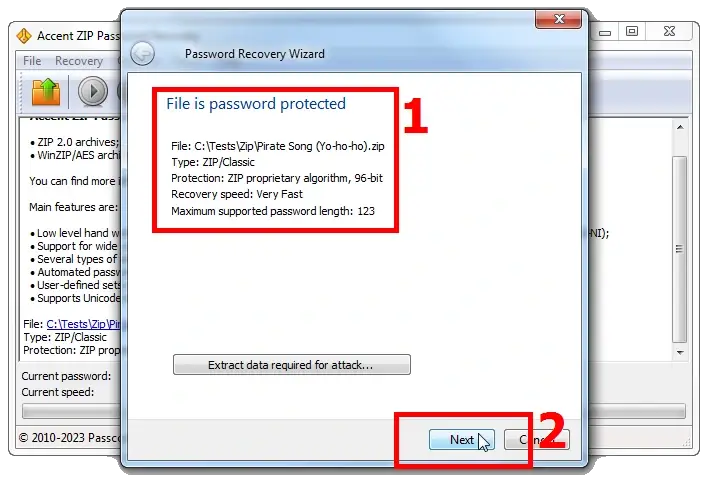
3. At the next stage, you can choose one of the three types of attacks to search for the lost password:
- Brute force attack (with a simple mask)
- Extended mask attack (with this one you can specify sets of characters for each position in the password)
- Dictionary attack (this attack allows you to combine up to four dictionaries and modify them according to your own rules)
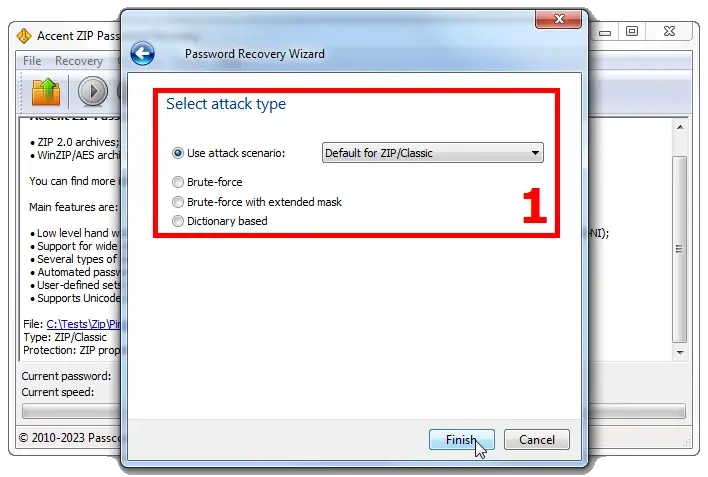
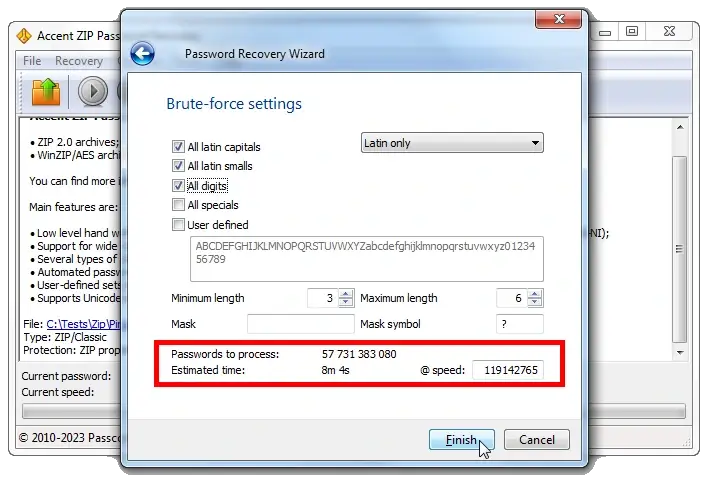
4❶. The most straightforward and penny-plain method, which may take as long as lifetime [life of the Universe? 😜], but definitely a successful one is brute force attack.
Set parameters for password generation, and the program will generate passwords and test them until the right one is found:
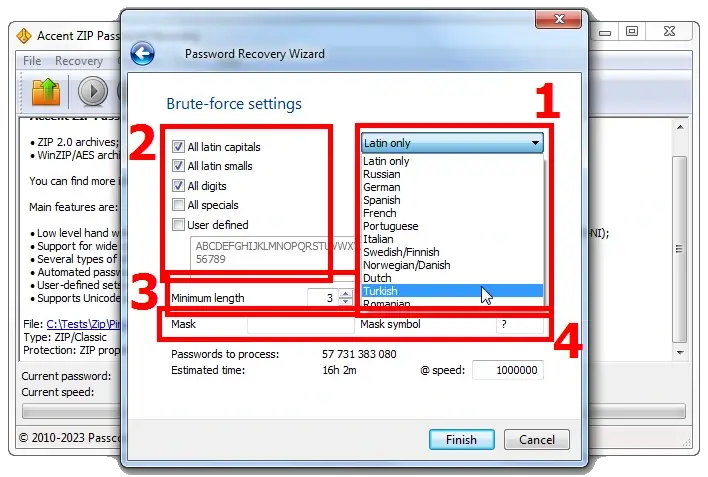
To use the brute force attack, you can (and it is recommended) to specify the following:
- Language alphabet
- A set of applicable characters (uppercase and lowercase letters, numbers, special characters); the set can be edited (option «User defined»)
- Minimum and maximum password length (you do remember the formula to calculate the range of possible passwords, don't you? 😜)
- Simple mask (the unknown parts of the password should be hidden under the «Mask symbol». Then each character from the defined charset will be tested as each masked symbol)
At this point the program will show the estimated number of options to test and the time it will take to go through ALL of them. The processing speed is based on previous password search sessions completed for archives.
4❷. A more advanced method is brute force attack with an extended (positional) mask.
What if you have an idea of the password structure, its composition and that different sets of characters can be used in different parts of it?
Here's the most primitive example: the password starts with an uppercase letter and ends with two numbers (for example Peace24).
Trying out the full set of characters (uppercase, lowercase, and numbers) in all positions would result in 3 521 614 606 208 generated passwords. However if in the first position you only test uppercase letters, then only numbers in the last two positions, and lowercase letters in the middle part, there would only be 1 188 137 600 options to try.
That is 2 964 times fewer. In other words, it's almost three thousand times faster!
You might not even have time to make a cup of coffee… 😉(see item below)
Unfortunately the mask description window in Passcovery programs cannot boast a very user-friendly interface. But if you figure it out, you can skillfully cut off redundant tests and save a lot of time.
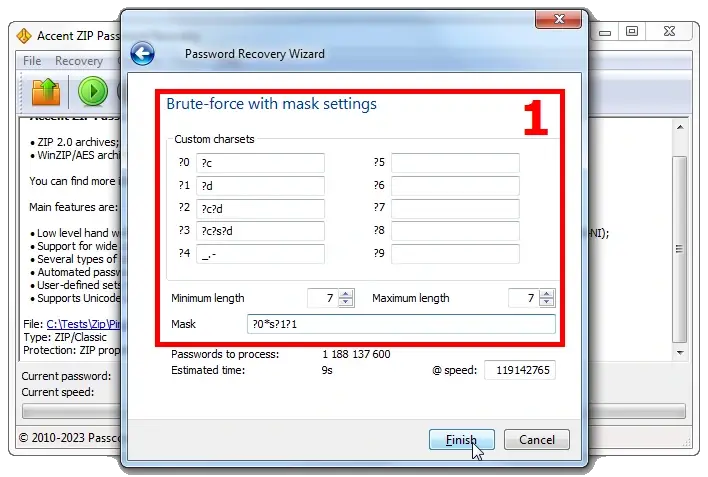
In the Passcovery knowledge base there is an article with how-to's and case studies about the extended mask option. To create a mask for your specific case see the how-to guide and feel free to reach out to the support.
4❸. Dictionary attack is the first method I recommend when nothing is known about the lost password.
There are many different dictionaries available online. They contain lists of popular passwords, passwords from leaks, passwords in different languages, etc. And there is always room for human foolishness (and/or carelessness). So no matter how strong protection may be, there is a chance the password is «1234»… 😁
Accent ZIP Password Recovery for Zip passwords (as well as Accent RAR Password Recovery for RAR passwords) allows you to enable up to three dictionaries and various mutations, defined by the developer.
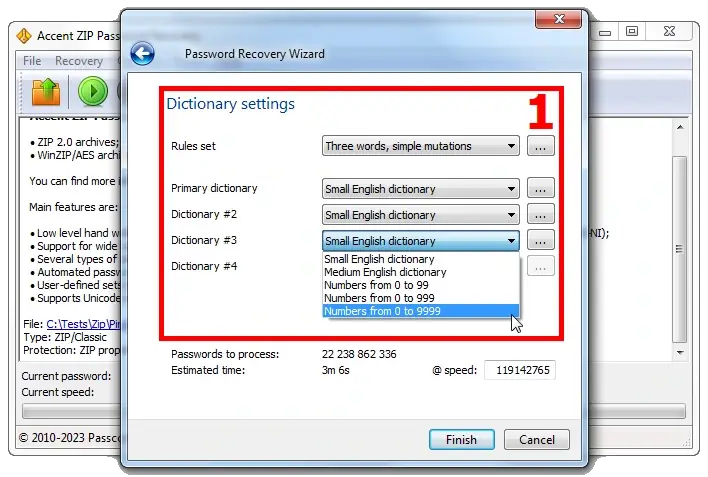
What puts Passcovery programs out of the crowd is the possibility to create custom mutations for dictionaries. The feature comes as super handy when you know that the password is a compound phrase consisting of several blocks.
In this case you can set a few rules for combining up to four dictionaries with the desired 'blocks' and their subsequent mutations according to the defined rules. The «Rule Editor» is another great tool that helps visualize the process of merging dictionaries and their mutation.
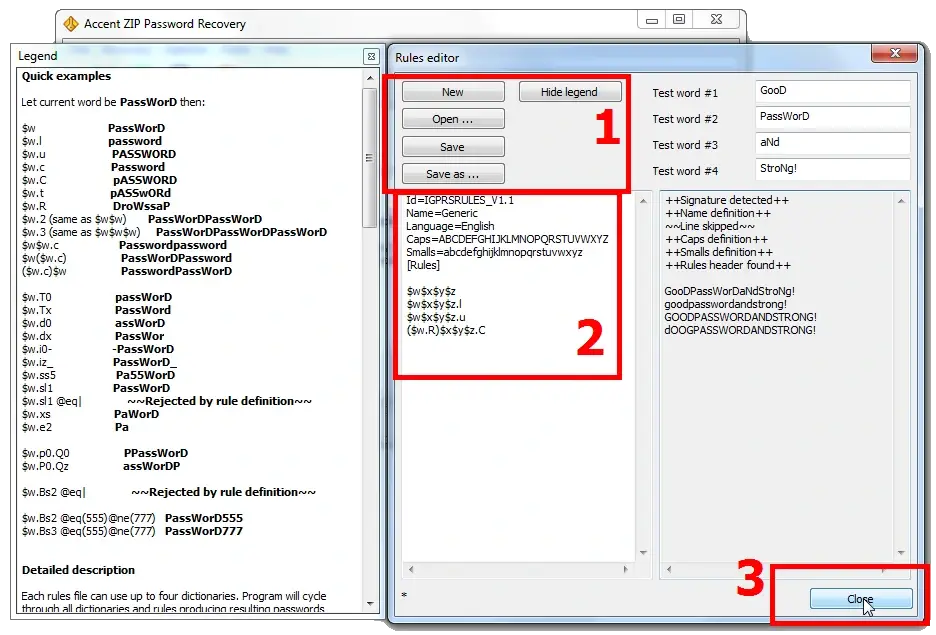
At the next step the rules and dictionaries are linked to the configuration of the dictionary attack. Here's a step-by-step how-to guide. Though the presented example is about recovery of an Apple iOS backup password using Passcovery Suite, but the interfaces are identical, remember?)
5. And that's about it. Once all the settings are done, we are good to start the search by clicking «Finish». The program will automatically adjust the processing speed and calculate the attack duration. It's the right time to brew yourself a cup of coffee…
The recovered password will be displayed as an imitation of a hyperlink. Click on it to copy the password to the clipboard.
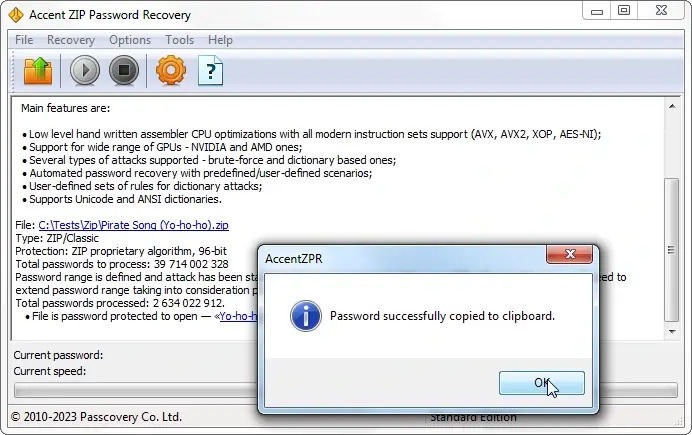
The password has been found, open the password-protected archive and delete the password from it, as recommended above.
Common Questions About Password-Protected Archives
Imagine you have a door at home with an "unbreakable" lock—at least that's what the manufacturer claims. You always secure it with this supposedly reliable super-lock, confident that only you can enter. But it turns out the lock has a vulnerability: a Master Key or some hidden sequence of actions that opens the door just as easily as your own key would. These hidden methods of bypassing security are exactly what we call backdoors.
Backdoors can be intentionally built in by manufacturers or appear accidentally due to flaws in the security system's design. Essentially, there are two ways to get into a house: through brute force (blow torch, saw, jackhammer), which leaves the door destroyed, or through a backdoor—quick and without any trace of forced entry.

A dictionary attack is a password recovery method where software cycles through values from a pre-compiled list: words, phrases, and common password variants. Unlike brute force, which checks every possible character combination, a dictionary attack uses only the most likely passwords, making the process significantly faster.
For ZIP and RAR archives, specialized utilities can test millions of words from the list per second. The method is especially effective when the password is based on real words, names, dates, or typical combinations like "password123" or "admin2026".

An archive password is a security measure that encrypts the contents of ZIP, RAR, and other compressed files. When you set a password, the archiving software applies a cryptographic algorithm: the data inside the archive is transformed into encrypted form and becomes inaccessible without the correct key.
To open or extract protected files, users must enter the password—the archiver uses it to decrypt the data. Modern formats such as RAR and ZIP with AES encryption provide a high level of security and reliable protection against unauthorized access.

7zip and the classic zip format are two different approaches to compressing and protecting files.
7zip:
- 7zip is a more modern and powerful archiver that supports a wider range of compression and encryption algorithms.
- It provides higher compression ratios compared to the classic zip format.
- 7zip also supports various encryption methods, including AES-256, which is considered one of the most secure currently available.
Classic zip format:
- Zip is one of the most widely used archiving formats.
- It typically offers less efficient file compression compared to 7zip.
- Zip also supports encryption methods, but their security level may not be as strong as 7zip's.
Overall, 7zip provides stronger protection and more efficient file compression than classic zip.

To open a password-protected ZIP file, use an archiving tool such as 7-Zip, WinZip, or Windows' built-in utility. Open the ZIP file, select the items you need, and begin extraction—the program will prompt you for the password. After entering the correct value, the archiver will decrypt the data and save the extracted files.
If you're working through Windows Explorer, simply double-click the archive and try to open any file inside: the system will automatically prompt you to enter the password before extraction.
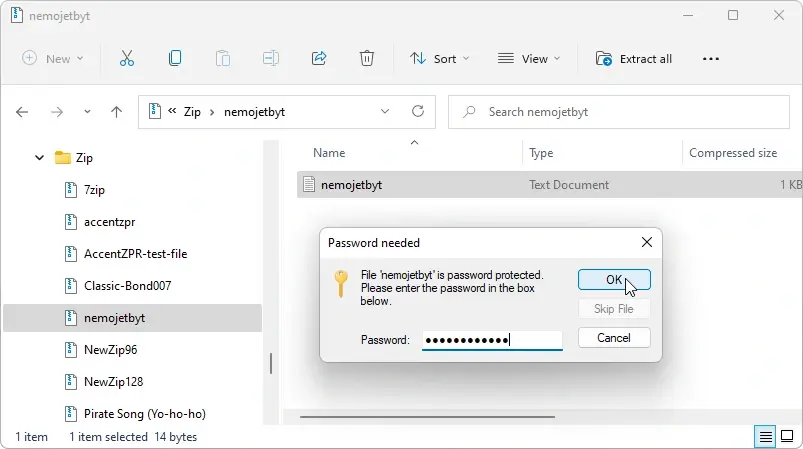
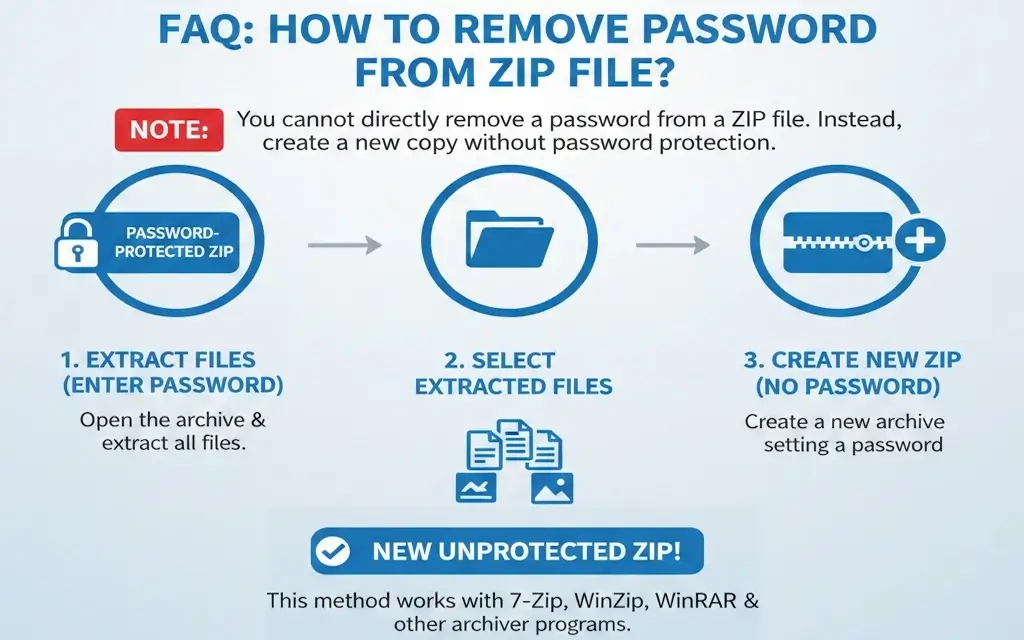
It's impossible to remove a password directly from within a ZIP file. To get an unprotected archive, you need to create a new ZIP file from the already-decrypted data. Here's how:
- Open the original ZIP archive and enter the password to extract all files.
- Create a new ZIP archive from the extracted data without setting a password during compression.
This method works with any archiving software—7-Zip, WinZip, WinRAR, and built-in OS tools. The result will be an archive with the same files but without protection.