Q: Where Is the Password in a ZIP File Stored, and How Does ZIP Check It?
A ZIP archive's password is never stored anywhere — not in the header or the body of the file. ZIP archivers use the password to generate an encryption key that protects the archive’s contents.
Let’s break down how it works.
How ZIP Verifies a Password: No Secrets, Just Math
Every time you enter a password, the ZIP archiver computes a unique encryption key.
Classic ZIP encryption, for example, uses a weak algorithm based on XOR and CRC32, whereas WinZip with AES encryption applies a robust PBKDF2 algorithm with 1000 iterations, making the calculations more complex.
This key is then used to either decrypt data or verify the archive’s integrity. If the key is correct, the archive opens; otherwise, the archiver prompts you to try again.
Think of it as a safe’s combination lock: you enter the combination (password), and the lock inside creates a unique key that opens the safe. The password is just the instruction for creating the key; it is never stored.
How ZIP Generates a Key from a Password
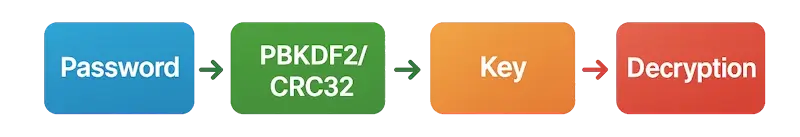
Why the ZIP Password Isn’t Stored, Even in Encrypted Form
Storing a password, even encrypted, is insecure — it's like leaving your car key in plain sight. ZIP archivers only use the password to generate a key, which is created dynamically "on the fly" by hash algorithms such as PBKDF2 or CRC32. The key itself isn't stored in the archive either. Obviously.
The exception is a quirk in the AES-256 implementation where passwords longer than 64 characters are hashed with SHA-1. This can cause a cryptographic anomaly: the archive can be opened with either the actual password or its SHA-1 hash in ASCII (not exactly a backdoor 😅).
Password Recovery: Brute Force Only
The same principle applies when recovering lost passwords: "Enter password" -> "Check password" -> "Repeat until success." There is only one way: try all possible combinations until the correct one is found.
Tools like Hashcat and Accent ZIP Password Recovery use GPU acceleration on NVIDIA, AMD or Intel graphics cards, as well as optimized attacks, to speed up the process.
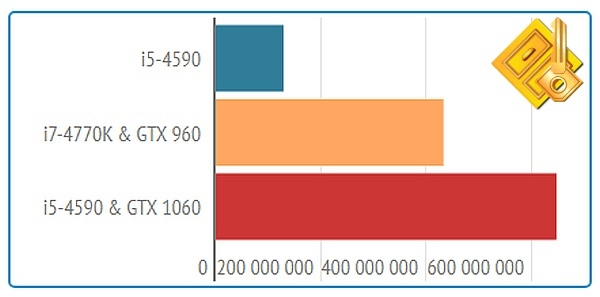
The main attacks for forgotten ZIP passwords remain unchanged:
- Brute-force — testing all possible combinations.
- Mask attack — speeds things up if you know the password’s structure (position-based attack in AccentZPR).
- Dictionary attack — for passwords from prepared lists of words, names, or dates (dictionary merge and mutation in AccentZPR).
Accent ZIP Password Recovery also supports ready-made and custom attack scenarios, saves attack progress, and has a command-line interface. It guarantees high speed on any PC. Details and a demo version are available on the Passcovery website.
 |
Accent ZIP Password Recovery for classic ZIP and WinZip AES archives |
25.04 | Download x64 (8752 Kb) |
|
|||
Three Common Questions About ZIP Passwords
The password is not saved. Instead, the archiver generates a key from the password using PBKDF2 or CRC32 and uses it to decrypt the data. If the key is correct, the archive opens; otherwise, a new password is requested.
The only option is to recover the password using tools like Accent ZIP Password Recovery or Hashcat. These tools use brute-force, mask, or dictionary attacks with GPU acceleration to reduce search time. Free demo versions allow you to test their capabilities.

It depends on the complexity of the password, the encryption method used (classic ZIP or WinZip AES), and the power of the hardware. Simple passwords (four to six characters) can be cracked in minutes with GPU acceleration, while complex ones take longer and may require range adjustments. Tools like AccentZPR offer optimized speed and targeted attack techniques.