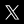RAR Password Recovery After a Ransomware Attack: What Are Your Chances?
QUESTION: Malware locked my files inside a password-protected RAR archive. Can Accent RAR Password Recovery crack this RAR password?
ANSWER: First, verify the file is an actual archive. Open it in WinRAR: does the program ask for a password? Great – the structure is intact. Getting an error like "The archive is either in unknown format or damaged"? That means the virus simply renamed your encrypted data to .rar, and no password recovery tool can help.
If the archive is genuine, everything depends on how the password was generated. Predictable algorithm – you can find it in hours. Cryptographically secure generator – even top-tier graphics cards won't help. Identify the virus type: that's what determines your outcome.
Two Types of Ransomware – Two Scenarios
Why do some passwords get cracked while others don't? It all comes down to the generation algorithm. "Lazy" viruses use predictable schemes: hardware hash, username, infection date. "Serious" ones employ a cryptographically secure PRNG (pseudorandom number generator), making brute-force mathematically hopeless.
Example of the first type: the CryptoHost virus (2016) generated passwords by combining hardware identifiers with the username. After BleepingComputer published their analysis, recovery became trivial: just replicate the algorithm, and the password is computed in seconds.
The opposite case: the Memento group (2021). According to a Sophos report, they generated a unique cryptographically secure password for each file and transmitted it to a remote server. Cracking such a password is impossible regardless of computing power.
RAR Password Cracking Speed: Real Numbers
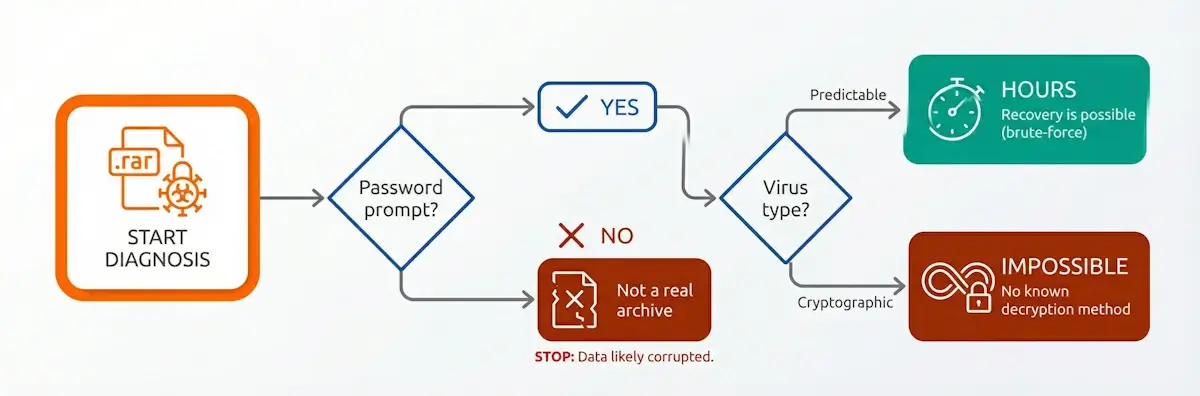
An NVIDIA RTX 5090 checks approximately 326,000 RAR5 passwords per second (current speed benchmarks). Sounds impressive? Let's do the math. A 10-character password using lowercase letters plus digits (36 options per position) yields 3610 combinations. A complete brute-force would take around 355 years.
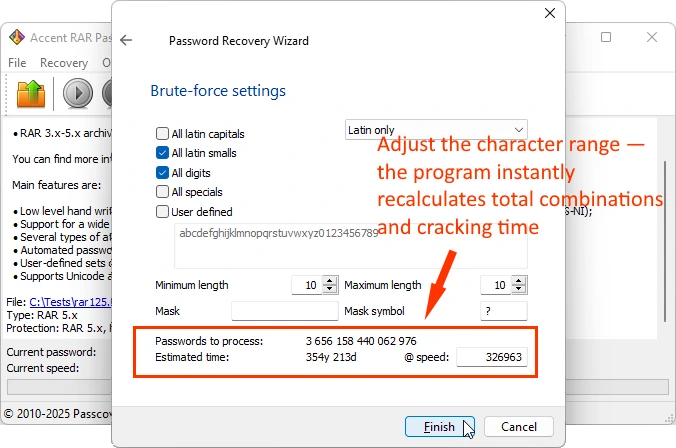
Guidelines for password length using the same character set (lowercase + digits):
- Up to 6 characters – hours of cracking
- 7 characters – days
- 8 characters – months
- 9 or more – years, decades, centuries
And that's with only 36 characters in the set. With full ASCII (96 characters), timelines become even more dramatic.
Cracking a RAR password is like fishing without bait. You can sit on the shore all day, but without knowing what the fish are biting in this particular lake, you won't catch anything. A clue about the password is your bait: find a pattern, narrow down the character set, and AccentRPR "reels in" results in hours instead of centuries.
How to Find a Password for an Infected RAR Archive
If you know something about the password structure or have found a clue, your chances increase dramatically.
"We had a case a while back: the password turned out to be something like
Denis Gladysh, head of Passcoveryabbbabaabaaababb. Looks impressive – 16 characters. But there was a hunch about a limited alphabet. So we started restricting the character set for password generation, and AccentRPR cracked it in a few hours. The key takeaway: any information about the password reduces brute-force time exponentially."
Where to start:
- Identify the virus. Upload your file to ID Ransomware or search for symptoms on Reddit (r/techsupport). Found the name? Google "name + password"
- Check your %TEMP% folder. Scripts with archiver launch commands may still be there, sometimes with the password in plain text
- Found a pattern? Configure a positional mask or dictionary mutations. This reduces the search space by orders of magnitude
The general workflow: open the archive, select the attack type, start the recovery.
Try it on your archive: download AccentRPR demo (10 MB, Windows x64).
Recovery Chances: Decision Table
| Situation | Action | Chances |
|---|---|---|
| Found a pattern or the virus's algorithm | Positional mask in AccentRPR | High |
| Password up to 7 characters, pattern unknown | Brute-force + dictionaries with mutations | Medium |
| Password 8 – 10 characters, some guesses about the character set | Mask based on known positions | Medium |
| Password 10+ random characters, no clues | Keep the archive, wait for a decryptor | Low |
Decryptors for older viruses are published on No More Ransom months, sometimes years later. The golden rule: don't delete the archive. Today's dead end might have a solution tomorrow.
Frequently Asked Questions About RAR Password Recovery
RAR is intentionally slowed down to resist brute-force attacks. In RAR3/4, the number of key stretching iterations
depends on password length. RAR5 uses a
KDF_count parameter to control cracking difficulty. Classic ZIP has no key stretching at all, while ZIP AES uses only 1,000 iterations compared to
32,768 in RAR5 (KDF_count=15, the 2026 standard).
| Format | Key Derivation (KDF) | Encryption | Load per Password | Cracking Speed |
|---|---|---|---|---|
| RAR3/4 | SHA-1 key stretching: sha1_blocks = 4096 × (2L + 11) |
AES-128 | SHA-1 rounds = 80 × sha1_blocks 4 chars → ~6.2M 10 chars → ~10M 28 chars → ~22M |
Very slow, increases with password length |
| RAR5 | PBKDF2 (HMAC-SHA256) 2KDF_count |
AES-256 | 32,768 HMAC-SHA256 blocks for KDF_count=15 | Slow, independent of length |
| ZIP Classic (ZipCrypto) |
No KDF (direct password use, CRC-32 based) | Stream cipher (vulnerable to known-plaintext) | ~0 crypto operations | Very fast |
| ZIP AES | PBKDF2 (HMAC-SHA1) 1,000 iterations |
AES-128/256 | ~1,000 HMAC-SHA1 blocks | Moderately fast |
Concrete numbers: an RTX 5090 tests ~326,000 RAR5 passwords per second versus ~61 billion for classic ZIP. That's nearly a 200,000x difference. For ZIP, this means accessible cracking. For RAR: a graphics card only reduces the time. The password structure decides the rest.
It depends on password length and available clues. See the decision table above: if the password is up to 7 characters or you have a pattern, cracking is worth attempting. A 7+ character random password with no clues – your chances are minimal.
General ransomware statistics: about 40% of those who pay never receive a working key. But that applies to viruses with custom encryption. If your files are in a genuine RAR archive (WinRAR opens it and asks for a password), getting that password guarantees you can extract your data. The only question is whether the attackers will actually send it.
Alternative: keep the archive. Decryptors are published on No More Ransom months, sometimes years later. When the key appears, you'll unpack the archive.
You can, but the speed difference is about 50x. An RTX 5090 tests ~326,000 passwords per second; a top-tier Intel Core Ultra 9 285K – around 7,100. A week of cracking on GPU becomes a year on CPU.
When CPU is acceptable: the password is up to 6 characters, or you have strong clues (exact character set, positional mask). Then the search space narrows enough that even a processor can handle it in reasonable time. For 6+ character passwords without clues – GPU is essential.
cn: 勒索软件攻击后能破解RAR密码吗?
pt: É Possível Quebrar uma Senha RAR Após um Ataque de Ransomware?
de: Kann man ein RAR-Passwort nach einem Ransomware-Angriff knacken?
ru: Вирус и RAR архив: возможно ли восстановить пароль?