A Case of Success: Apple iOS 10.2-13.x Backup Password Recovery Using Mutated Dictionary Attack
The release of Apple iOS 10.2 has enormously increased the amount of calculations and time required to complete brute force attack. Because of lowered speed of brute force, it's become [almost] impossible to crack someone else’s password for iPhone/iPad backup file.
But you can still restore your own iOS backup password.
Below are some tips on what tool and settings to use and how to do it successfully.
Having updated from iOS 12.4 to the more buggy iOS 13.2.2 one of our Passcovery Suite user asked us to help restore a forgotten password for iPhone backup file. The password to be recovered is a compound phrase consisting of three components (word-numbers-word). We know the range of possible combinations of words and numbers (fre, frett, 2323, 2424), but the spellings can vary (jumping ahead a bit, we got the total of 7000 passwords to be tested). Manual brute forcing yielded no results.
Passcovery Suite with its dictionary-based mutations can handle the task in 10 minutes.
Here is how you do it.
The case under consideration can be applied to all Passcovery programs as they all have the same functionality and unified interface.
Apple iOS Backup Password Recovery. Step By Step Guide
When recovering passwords with dictionary attack you need to complete the following three steps:
Creating a project
1. Create a new folder that will contain all the attack-related files. Now you can keep everything under control and you won't accidentally lose your backup.
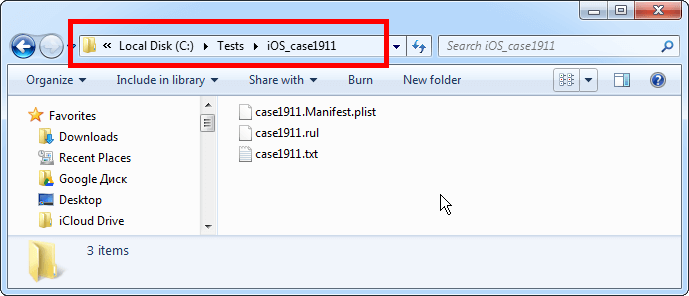
2. Find the manifest.plist file in the backup and copy it to the project folder. That is the file that contains the encrypted password – the one to be attacked.
Standard location of iOS backup files:
C:\Users\(username)\AppData\Roaming\Apple Computer\MobileSync\Backup\
Creating a word-list (dictionary)
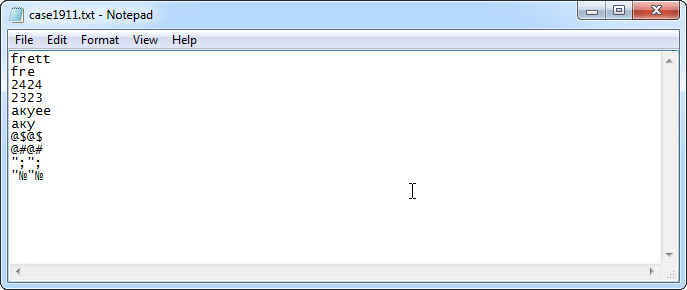
1. Follow the instructions and create a Unicode dictionary. Extend the word-list with all possible variations of alphabetic and numeric arrays that make up the password. Make sure you include some frequent typos: uppercase/lowercase letters, keyboard layout errors, pressed Shift key error.
Save the file to the project folder.
Case errors (uppercase/lowercase letters) of the first letters can be taken into account later when creating mutation rules for passwords from the dictionary. You can do this in Passcovery programs.
In our case (word-numbers-word), we have quite a small dictionary. That is why it will include both parts of the password – a «words» and «numbers». In the case of a more complicated password structure, it is recommended to set an individual dictionary for each part.
2. Run Passcovery Suite and create a set of mutation rules in the program to allow generation of various passwords from the dictionary. You can glue up to 4 dictionaries together, define rules for combining words into one and transforming the resulting password before it is tested.
Using «Rules Editor» in the program menu:
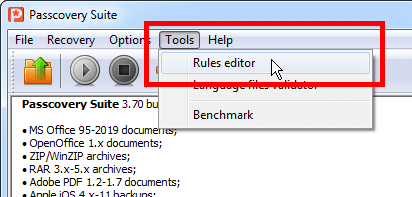
Click «New» to create a new set of rules and describe the required rules with macros [1]. For more convenience you can open the macros hint bar – «Show legend» button [2]. You can preview mutation of entered words based on each mutation rule as it is instantly displayed in the preview window [3].
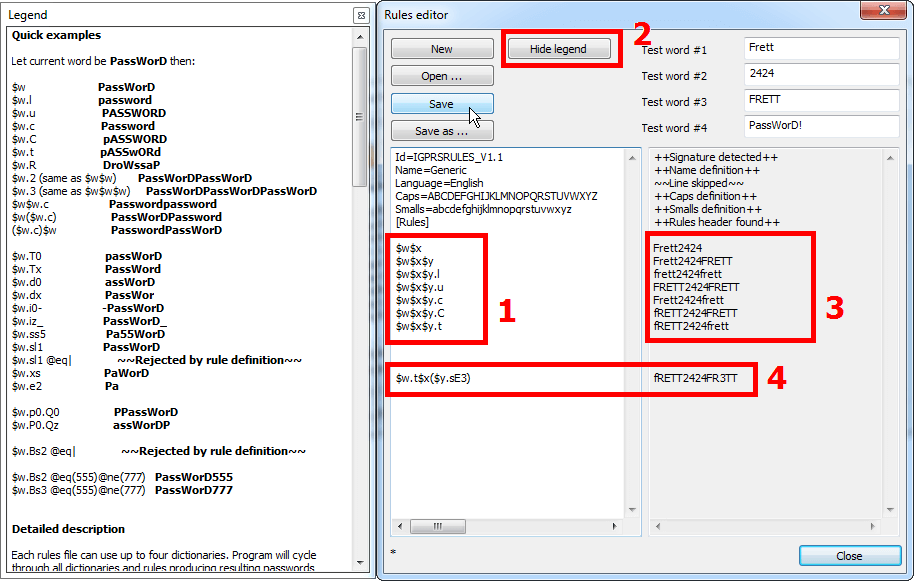
Please note: every single change of words should be described in a separate line. New line → new rule → new password.
At this point you can factor in first letter case errors by specifying the relevant macros.
In our case the following set of rules will be used:
- $w$x – 2-part password from two dictionaries without mutations
- $w$x$y – 3-part password from three dictionaries without mutations
- $w$x$y.l – password from three dictionaries, all letters being changed to lowercase
- $w$x$y.u – password from three dictionaries, all letters being changed to uppercase
- $w$x$y.c – password from three dictionaries, the first letter is a capital one
- $w$x$y.C – password from three dictionaries, the first letter is a lower-case letter
- $w$x$y.t – password from three dictionaries, letter case of all letters being changed
See the complete guide to word mutation macros in the user manual.
You do not necessarily have to apply mutations only to the overall result. Mutations can be applied to each dictionary separately. For example:
- $w.t$x($y.sE3) – reverses letters from the first dictionary and replaces the character E with 3 in the third dictionary [4]
When everything is ready and mutation rules are set, save the rules file in the project folder.
Running password attack
We are done with preparation steps. Let's get your iPhone password recovered!
1. Start Passcovery Suite and open the Apple iOS backup file with encrypted password, i.e. the manifest.plist file from the project folder
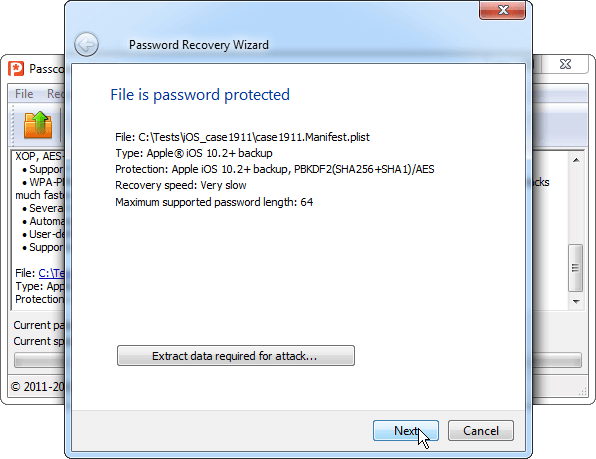
2. Passcovery Suite displays information about file format and enabled protection. Click «Next»
3. Passcovery Suite offers you to choose one of the three password attacks or a ready-to-use scenario. Select «Dictionary Attack» and click «Next».
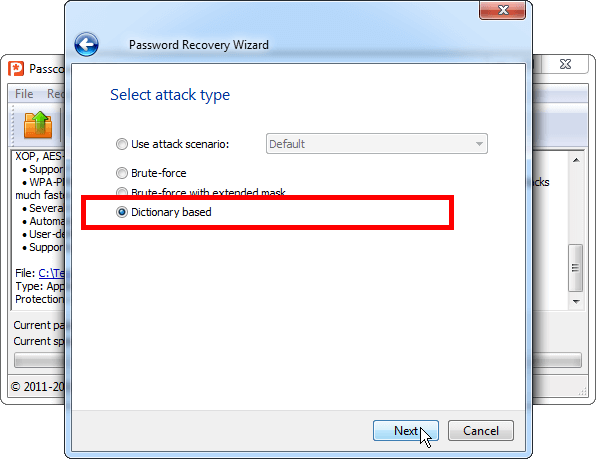
4. In the dictionary attack settings, first select the rules file that we saved earlier in the project folder [1].
As we have defined in the rules file, Passcovery Suite will enable selection of three dictionaries. Select each of the three dictionaries that we have compiled and saved in the project folder [2]. Click «Finish» [3]:
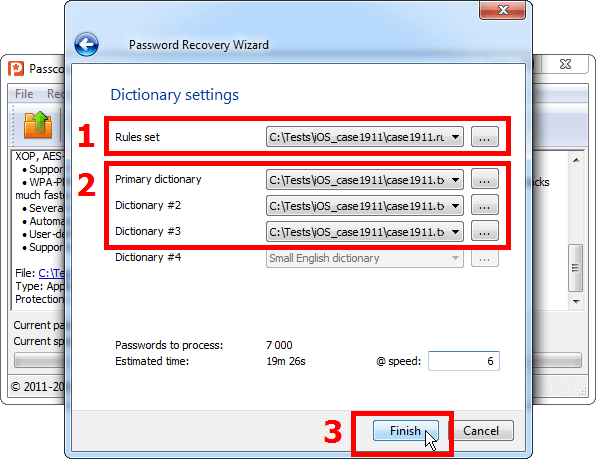
5. Passcovery Suite will start password attack according to the defined rules. The program will import passwords from three dictionaries, combine and modify them and test the generated passwords. It will continue until all passwords have been tested (in our case, the total of 7000 combinations will be generated from the dictionary with 10 passwords), or until it finds the lost password for Apple iOS backup file of your iPhone or iPad.
When it comes to Apple iOS backups, the speed of brute-force can be increased by using GPU calculations on graphics cards. Passcovery Suite supports GPU acceleration on NVIDIA and AMD graphics cards.
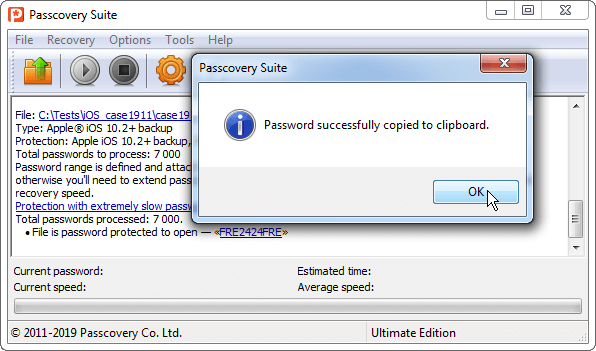
Once the password is found, the program will display it as a pseudo-link. Copy it to clipboard by just clicking on it.

What It Takes to Successfully Search Apple iOS Backup Passwords
No matter how complicated and lengthy the process might be due to the latest Apple iOS updates, it is still possible to restore one's own Apple iOS backup password.
To improve your chances, you have to clearly define the structure of your password and use a high-speed tool that can generate a range of words strictly according to the specified criteria.
That way you cut the number of calculations down to an acceptable level and get them completed as soon as possible – exactly as demonstrated here by Passcovery Suite in the case of Apple iPhone backup password.
More details and free demo:
| Passcovery Suite for Apple iOS backups, Microsoft Office, OpenOffice, LibreOffice, Adobe PDF files, Zip, RAR, TrueCrypt, WPA/WPA2 |
3.7 | Download x86 (14768 Kb) |
Download x64 (16880 Kb) |
|
| ||||