Extended Mask attack when the structure and symbols of the password are known
Our customer asks:
«I know the structure of my password and symbols it is composed of. Here is the PDL (Password Definition Language) description: [gG] [oO0] [oO0] [dD] [\. \0] [tT] [iI1] [mM] [eE3]
This means I need to generate and test all passwords from goodtime to G00D.T1M3
Can I do this in Passcovery software and how?»Surely, you can! This task can be solved with Extended Mask attack available in all Passcovery programs.
Here is what you need to do:
1. Run the program (in this example we use Passcovery Suite), select the file. You will see document protection information then:
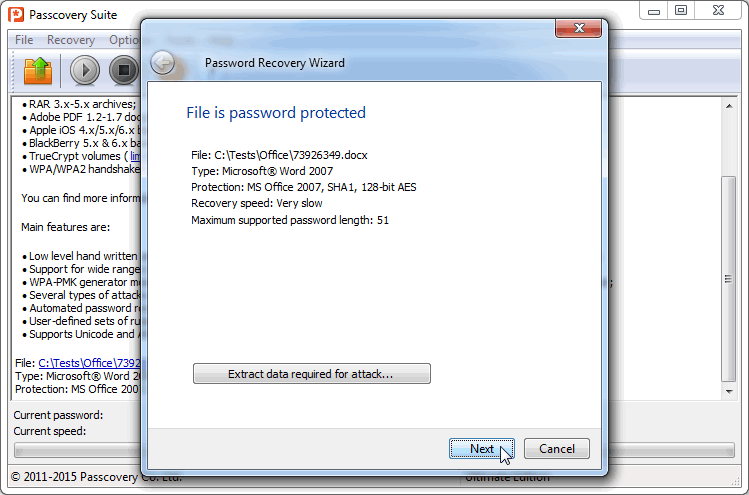
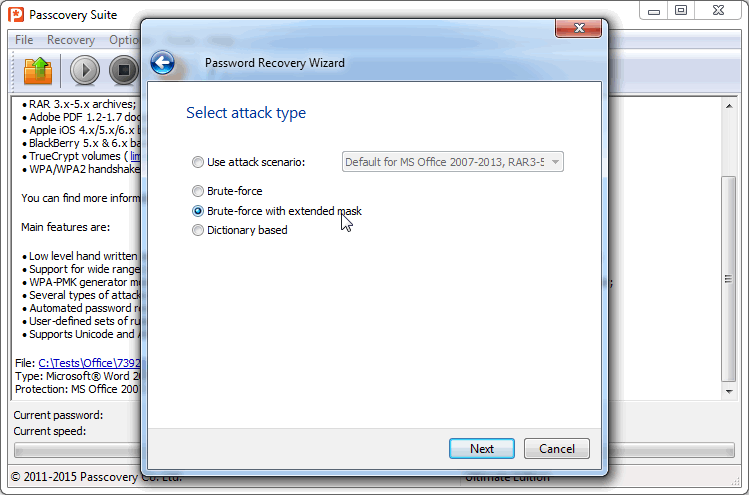
2. Click «Next» and select the type of attack — Brute-force with extended mask:
3. One by one specify all possible mutations of symbols in your password (gG, oO0, and so on), just like you did in PDL. Then, using the built in macro-language, combine them in the right order — ?0?1?1?2*3?4?5?6?7. Increase the maximum password length to 9 symbols:
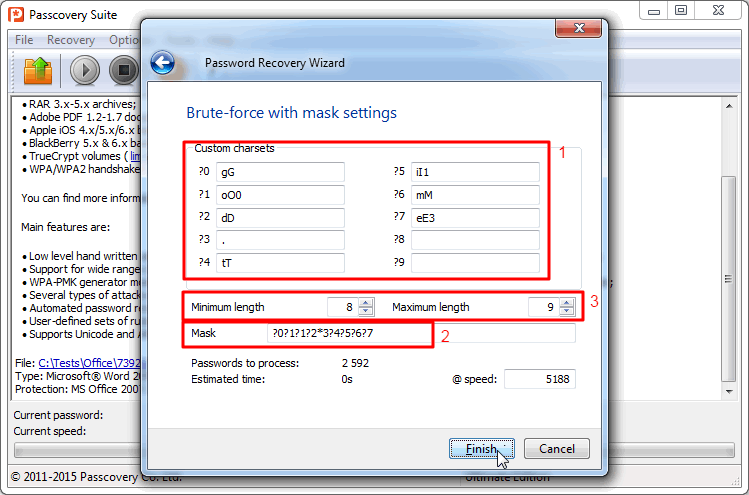
The [?] macros means a set of symbols is obligatory during password generation.
For instance, in our example (?0?1?1?2*3?4?5?6?7):
?0 – for the first position in the password only symbols of the #0 set — g or G — are used;
?1 – for the second and third positions — only symbols of the #1 set — o, O or 0 are used;
and so on.
The minimum password length is 8 symbols. The password cannot be shorter, because we use 8 obligatory symbols in the mask.
The [*] macros means the set is not obligatory. It is used for non-described symbols when the length of the password exceeds the length of the mask. In our example (?0?1?1?2*3?4?5?6?7):
*3 – symbols of the #3 set are used only if the password length is more than 8 symbols to ‘fill up’ space between obligatory symbols.
Put differently, for a 8-symbols password the program checks all variants without [.], and for 9-symbols it adds symbols for the #3 set and also checks variants with [.].
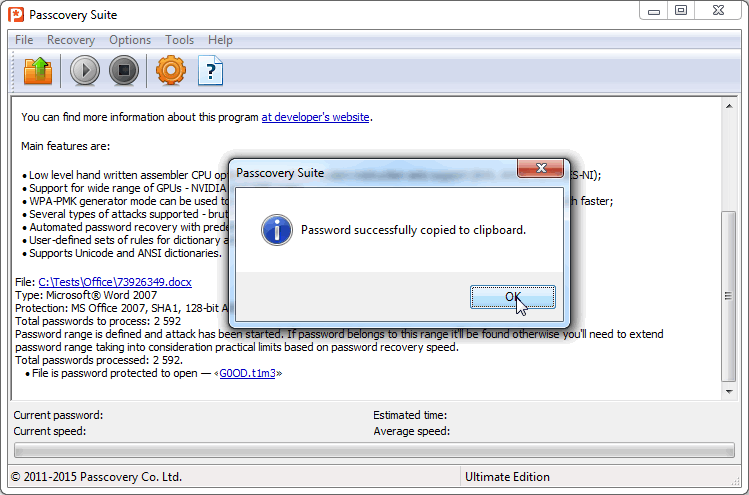
4. Click «Finish» and wait while all the variants specified by the mask are tested. If the password fits the mask, the program will find it and displays on the screen. Click the password to copy it to the clipboard:
Recover lost passwords with Passcovery:
Passcovery guarantees fast-paced password recovery on AMD/NVIDIA video cards. Our solutions:
Accent OFFICE Password Recovery — for Microsoft Office/OpenOffice passwords
Accent PDF Password Recovery — for Adobe PDF passwords
Accent ZIP Password Recovery — for Zip/WinZip passwords
Accent RAR Password Recovery — for Rar/WinRar passwords
Passcovery Suite — for Microsoft Office/OpenOffice, Adobe PDF, Zip, Rar, Apple iOS/BlackBerry, TrueCrypt, WPA/WPA2 passwords
More information and free demos of the products can be found on Passcovery websites.