How to Recover an OpenOffice Password with Dictionary Attack
Here’s a problem: a user forgot his password for a file created in OpenOffice Writer.
We need to recover the password and regain access to encrypted data.
OK, let’s crack it! :)
I am going to use Accent OFFICE Password Recovery from Passcovery and here’s why:
- it is a universal password recovery solution compatible with all versions of OpenOffice/LibreOffice/Microsoft Office
- it has the same user interface as password crackers for other file formats
- the program accelerates on AMD/NVIDIA graphics cards
Accent OFFICE Password Recovery offers three types of attack for recovering passwords:
- Brute-force attack — sequential testing of each password
- Brute-force attack with extended mask — direct search based on a specific positional mask
- Dictionary attack — sequential testing of passwords from a number of wordlists called dictionaries
I’m going to go with a dictionary attack. First a simple attack and then a more complicated one. I want to show you how to alter dictionary entries using Accent OFFICE Password Recovery and how to merge several dictionaries.
Examples below will show you how to crack a “Password to Open” for OpenOffice. Same way passwords for other formats can be cracked since all Passcovery apps have the same interface and functionalities.
Now here’s your user guide.
- Simple dictionary attack
- Dictionary attack with mutations
- Advanced dictionary attack with customized mutations
Simple Dictionary Attack
1. Run the program, open a password-protected file (for example this one), read the information about the file format and the protection method:
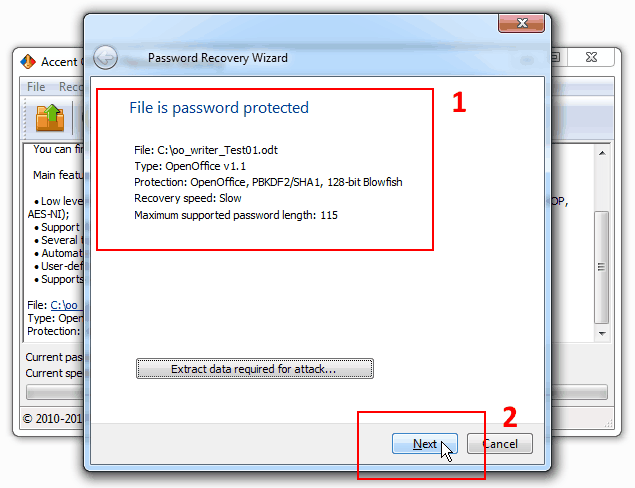
Click “Next”.
2. Select “Dictionary attack” and click “Next”:
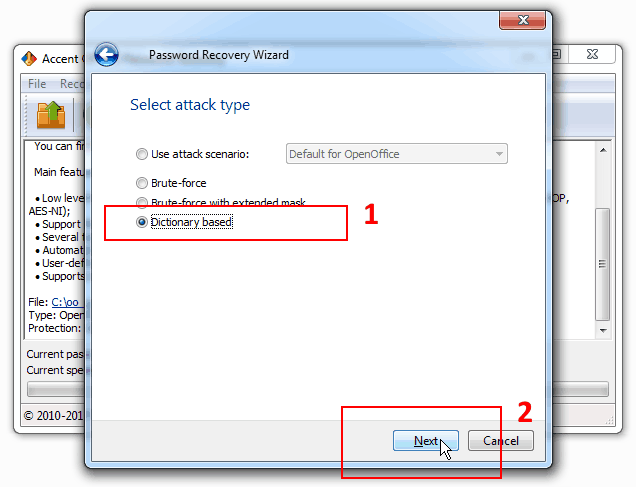
Besides password attacks AccentOPR offers a few recovery scenarios. The scenarios comprise various attacks consecutively performed by the program. Along with automated recovery options by default AccentOPR allows users to create their own recovery scenarios — read more about attack scenarios.
3. Choose a dictionary file (one from the list or, for example, the dictionary top1000000 most popular passwords) and start a password attack by clicking “Finish”:
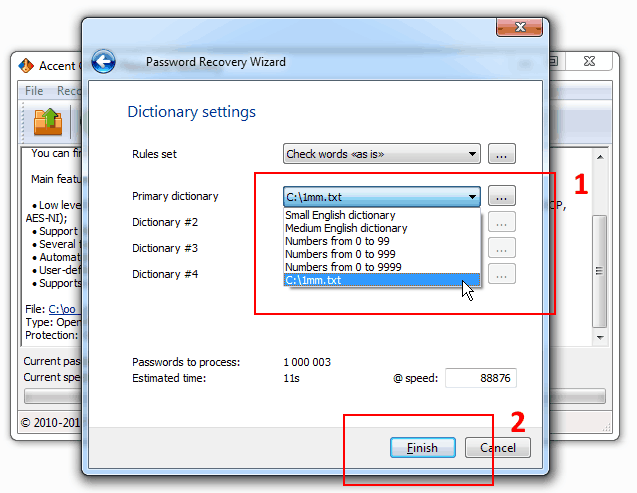
That’s how your launch a simple dictionary attack using a selected dictionary. The program will consistently read the passwords from the dictionary “as they are” without modifying them.
Dictionary Attack With Mutations
Dictionary attack will only work out if the password is among the words contained in the dictionary. However oftentimes we complicate our passwords by making multiple-word phrases or adding digits to them.
AccentOPR can crack such complex passwords.
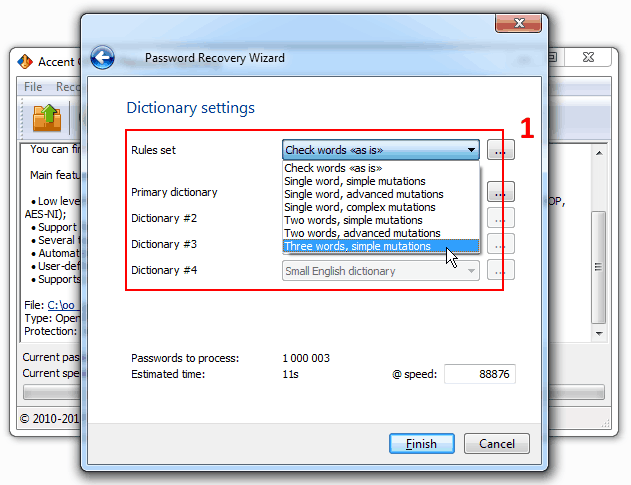
1. The program lets you choose certain password mutation (changing) rules for dictionary attacks:
- Various mutations of a single dictionary
- Various mutations of two dictionaries simultaneously
- Simple mutation of three dictionaries simultaneously
2. Depending on your chosen mutation rules please select one, two or three dictionaries to be used for generation and testing of OpenOffice passwords.
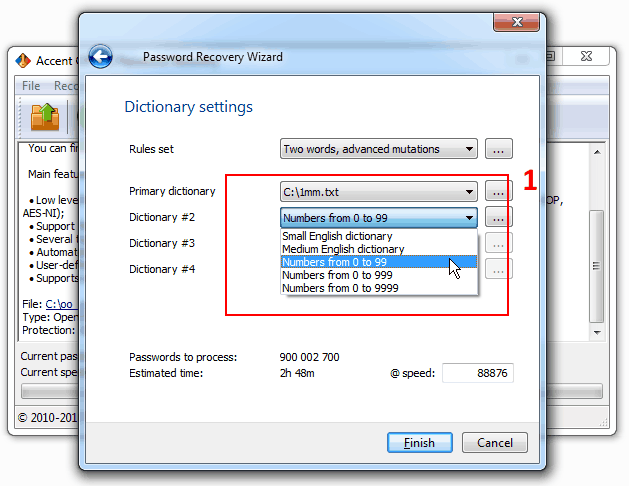
AccentOPR offers built-in dictionaries — two short ones with words (2232 and 27207 words) and three dictionaries with digits (0-99, 0-999 and 0-9999). You can either use the built-in dictionaries or link your own ones up.
Combine your own, more comprehensive dictionaries with ready-made numerical dictionaries. That’s how you can try passwords beginning or ending with digits. Here’s an example:
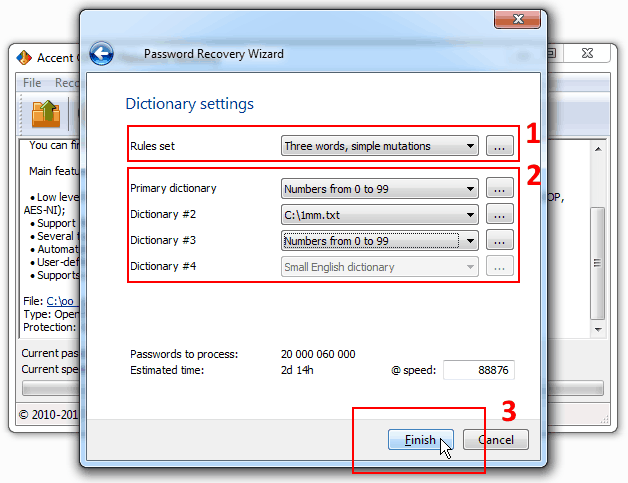
AccentOPR generates and tests the passwords “DIGITS1DICTIONARYDIGITS2”, where DIGITS1 — digits 0-99, DICTIONARY — passwords from a linked up dictionary, DIGITS2 — digits 0-999.
3. Run the attack by clicking “Finish”.
Advanced Dictionary Attack With Customized Mutations
Combining several words into one password is of course a great idea. But there may be more complex cases. Sometimes we substitute characters, transpose them, change lowercase to uppercase etc.
Password crackers by Passcovery are ready to take on the challenge. :)
1. Start AccentOPR and go to “Rules editor” (“Tools” menu):
2. Use macros to create your own mutation rules (manual). Show a chart legend for your own convenience.
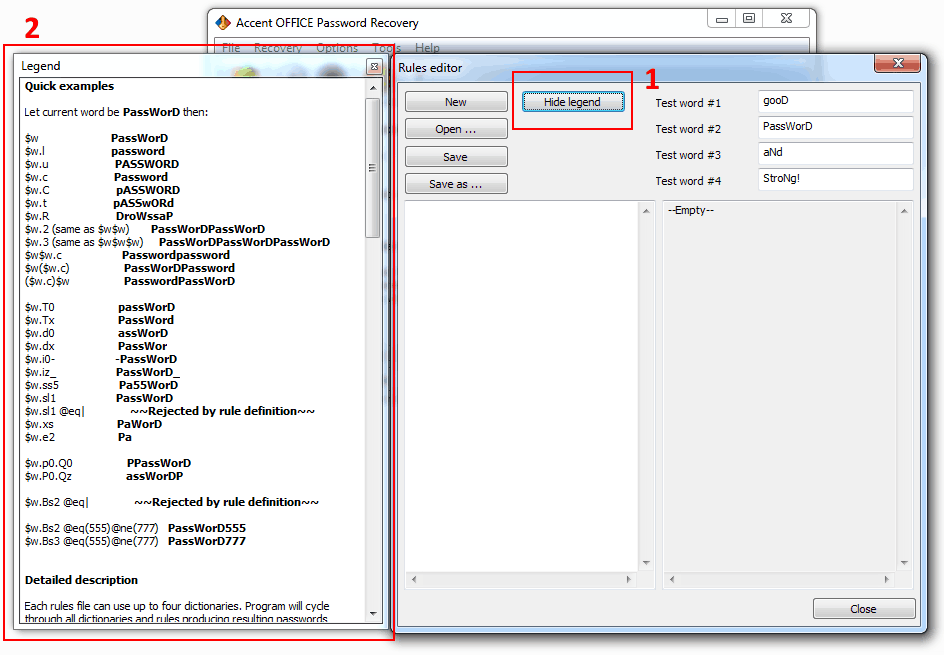
Each mutation rule is written in a separate line, there can be as many mutations (lines) as you may need. The program will consecutively execute all the configured rules, line by line.
For user convenience rules editor is equipped with a preview box where all the enabled rules are immediately applied to sample words and the results of mutations are clearly displayed. Each of the sample words symbolizes one of the four dictionaries. Yes, using macros you can define rules for simultaneous processing of several dictionaries.
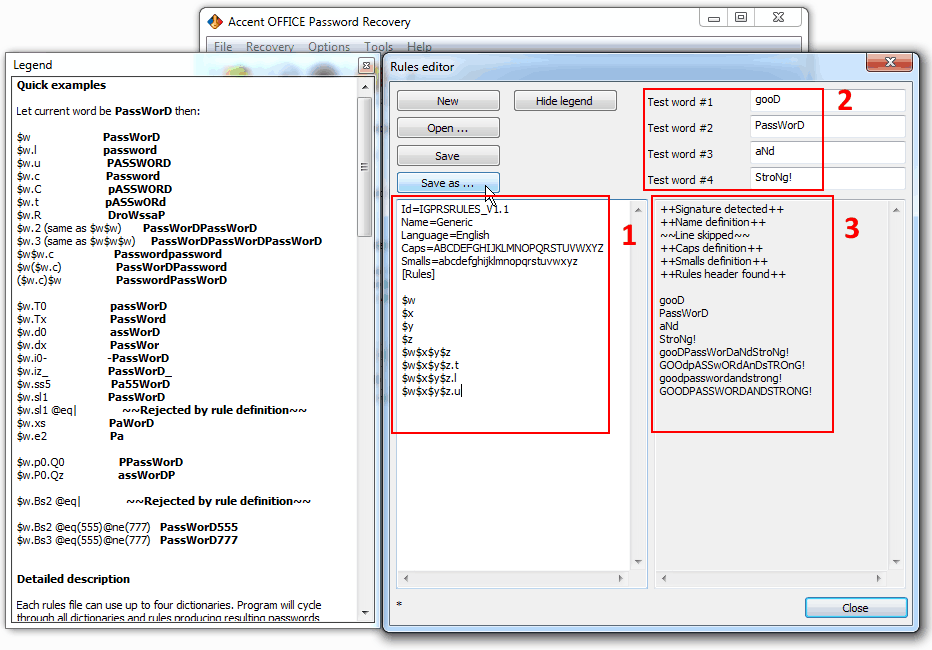
3. Once you’ve created and fine-tuned your mutation rules you might want to save them to a file for further use.
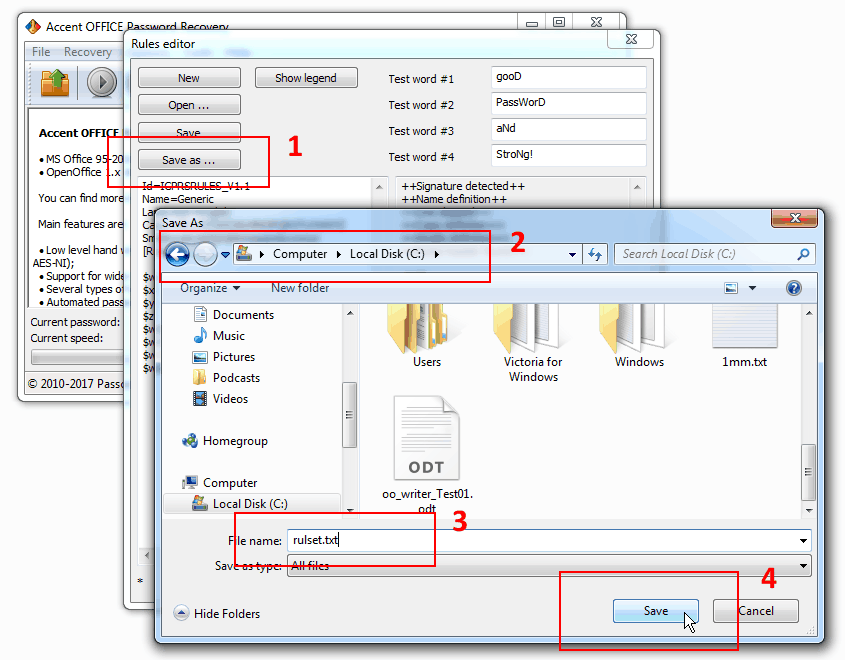
4. Open your password protected OpenOffice file, select dictionary attack and enable your set of rules by specifying path to the file you saved in the previous step, then set the required number of dictionaries:
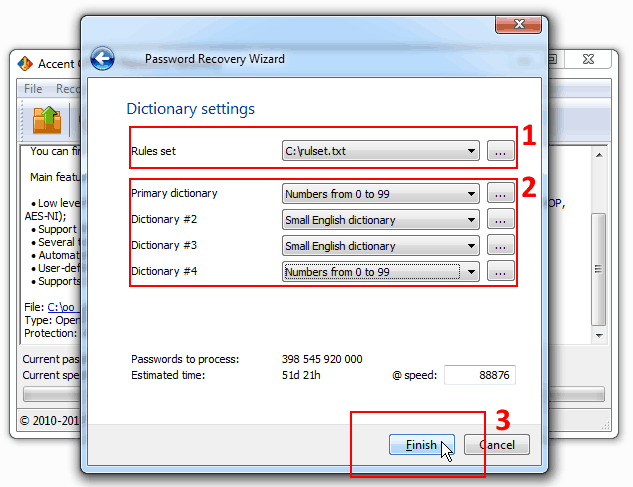
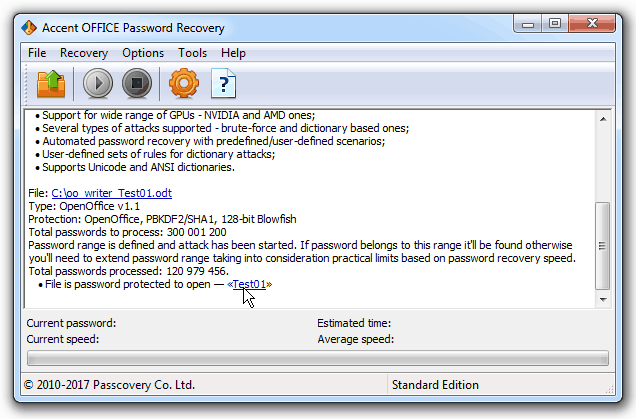
5. Run the OpenOffice password attack
If any of the enabled dictionaries contain the original password and the mutation rules are defined correctly, then AccentOPR will generate a correct modification of the password and display it on screen:
Additional Resources
Demo video: “Dictionary attack in Passcovery: dictionary mutation”
Demo video: “Dictionary attack in Passcovery: how to glue words from different dictionaries”
Download dictionaries: sets of dictionaries.
Three 'How' Questions About OpenOffice/LibreOffice
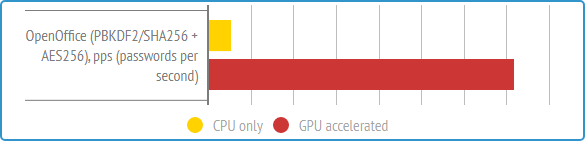
All such programs operate using a method called 'brute-forcing,' which involves trying out various combinations. The best ones utilize GPU acceleration on AMD/NVIDIA graphics cards.
There are several types of password attacks:
- Brute Force Attack: Trying out all possible combinations
- Mask Attack: Attempting combinations for the unknown part of the password
- Positional Mask Attack: Trying combinations with a known password structure
- Dictionary Attack: Testing combinations from a pre-existing dictionary
- Mutated Dictionary Attack: Combining dictionaries, mutating the generated variants, and checking them as potential passwords
To encrypt data in OpenOffice/LibreOffice, a combination of PBKDF2/SHA256 algorithms (to derive the key from the password) and 256-bit AES (for actual encryption) is used. Hence, the only way to gain access is through a brute-force method.
In brief: professional manipulation of the verification range and using exceptionally fast Passcovery-software.
The time it takes to recover a lost password, which essentially involves trying out all possibilities, depends on two factors:
- The number of password variations to check
- The speed of the verification process itself
Here's how you can expedite the process:
1. Manipulate the number of passwords to be checked. You can do this by using positional attacks for brute-forcing or by combining and modifying suitable dictionaries for dictionary attacks. This will reduce the range of checks to reasonable sizes. Fewer checks mean quicker results.
2. Utilize optimized software with GPU acceleration support for NVIDIA and AMD graphics cards. This will extract the maximum speed from your computer. The faster the verification, the shorter the overall cracking time
- Open Your Passcovery Program: Start by launching the Passcovery program and loading the password-protected file that you intend to decrypt
- Review Protection Information: Take a moment to review the document's protection information. This will help you decide which attack method to use
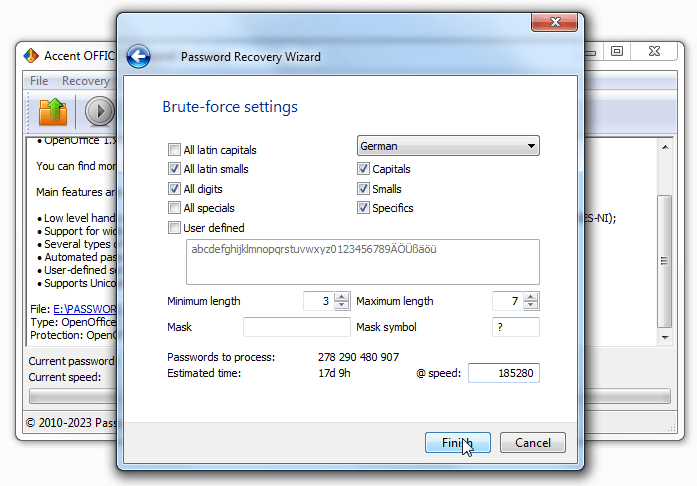
- Select 'Brute-force': From the drop-down menu of available attack methods, choose 'Brute-force'
- Choose Character Sets: Select the character set you wish to use for generating passwords. Typically, Latin characters are the default choice
- Enable Character Sets: Activate the character sets you want to include in the attack. This can encompass uppercase letters, lowercase letters, numbers, and special characters
- Customize Character List: For more control, turn on 'User-defined' mode. This allows you to modify the character list. Remove any characters that are irrelevant and add any that you suspect might be part of the password
- Set Password Length: Specify the minimum and maximum password length. This defines the range of passwords that will be generated and tested during the attack
- Use a Password Mask (If Known): If you have partial knowledge of the password, you can employ a simple password mask. Enter the characters you know and use placeholders for the unknown ones
- Evaluate the Impact: Before starting the attack, take a moment to assess how changes in your settings affect the number of passwords to check and the estimated time required for the brute force attack
- Launch the Attack: When you're ready, click 'OK' to initiate the brute force attack
By following these steps, you can tailor your attack to suit your specific knowledge of the password and the characteristics of the protected document. This approach increases your chances of success while minimizing unnecessary effort.