Recovering a password for a TrueCrypt disk
Step-by-step instructions to recover passwords to TrueCrypt disk drives.
Here you will learn how to extract the data needed to find passwords for encrypted disks and learn how to save time when recovering TrueCrypt passwords.
Statement of the Problem
You have a disk encrypted with TrueCrypt. However, you have lost the password needed to decrypt the TrueCrypt disk.
You need to:
- extract the data needed for password recovery
- recover the TrueCrypt password as fast as possible
It does not matter whether the disk is installed on internal or external media (HDD, SSD, USB-drive). Differences in disk encryption options:
- Encrypted logical disk. Here, in this example, we have a 2GB USB drive.
- It is an encrypted physical disk (WDE - Whole Disk Encryption - mode). We also have an external 40GB HD with a system partition containing an installation of Microsoft Windows. It is connected to a production system via USB.
We will consider both options.
Extracting data to attack the TrueCrypt password
To validate the attempted passwords, we need 512 bytes of data from the TrueCrypt disk. Depending on the type of encrypted disk, these values are stored with different offsets:
- Encrypted logical disk. These data are stored in the zero sector of the logical disk (offset 0x00)
- Encrypted physical disk. The data are located in the 63rd sector of the physical disk (offset 0x7c00 (62*512)). The TrueCrypt loader (bootloader) is located in the primary sectors.
We will use a program to copy the disk byte-by-byte in order to extract a data dump. This is similar to the dd command on Unix systems — dd for Windows.
Let's start.
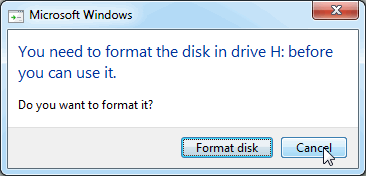
Step 1. Connect the external disk that is encrypted with TrueCrypt.
Window will report that the disk is damaged, and it will offer to format it. Cancel the formatting request:
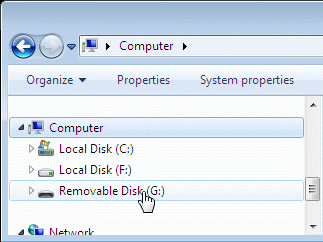
The system will display a new disk with an assigned letter. Here it is Disk G: for the logical disk and F: for the physical disk.
Step 2: Download and unzip dd for Windows.
The program is downloaded as a ZIP archive. Unpack it to a separate folder. Here it is the folder "C:\dd\"
Step 3: Launch the command line interface and go to the folder containing the program "dd for Windows".
Open the Start menu, enter "cmd" in the search box, right click on the found shortcut and select the option "Run as administrator":

Enter the command cd <path to program folder> in the command line interface window. Here it is the folder "C:\dd\"
Step 4 - Discover the system name of the connected disk.
Enter the command dd --list, and you will see a list arranged by size of all the connected disks that the system can detect (here the size of the physical disk is 40 GB):

Here we have already specified the system link to path linking the disk to the system. It is required in order to address the physical disk. Here it is \\?\Device\Harddisk1\DR1

It is not necessary to identify the system name of the logical disk. It can be addressed using its assigned disk letter.
Step 5: Extract data in order to recover the TrueCrypt password.
Enter and execute the command dd if = <[system] path to disk> of = <filename> <number of sectors>
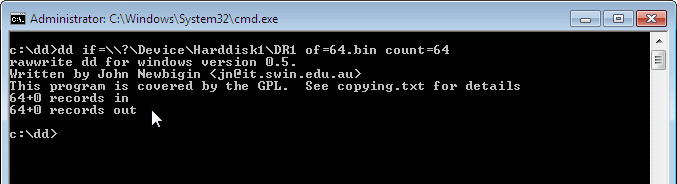
Here it is:
- here it's dd if= \\.\g: of=1.bin count=1 for a logical disk. We copy from the beginning of the logical drive G: to the file 1.bin (1 data sector).
- here it's dd if= \\?\Device\Harddisk1\DR1 of=64.bin count=64 for a physical disk. We copy from the beginning of the disk with a particular system name to the file 64.bin (64 data sectors).
You will now see two files in the folder with the program "dd for Windows": 1.bin and 64.bin, which were extracted from the encrypted TrueCrypt disks.
In order to make sure that we have extracted the required data from the physical disk, we open the resulting file (here it is 64.bin) in the HEX Editor. If everything was done correctly, we will see the "TrueCrypt Boot Loader" token:
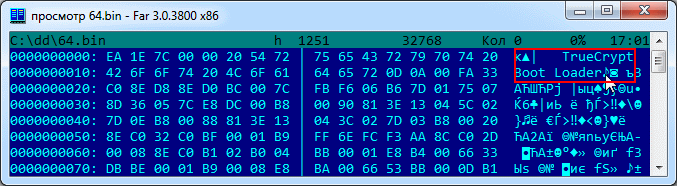
If we see nothing when we view the logical disk, then we will see a chaotic set of data.
Once we obtain the data needed to attack the TrueCrypt password, we can proceed to the second stage.
Recovery of TrueCrypt Password
THIS IS CRITICAL: TrueCrypt uses strong encryption algorithms and tricks that slow down the password checking process. Thus, you will not achieve fast speeds when brute-forcing passwords using any software. Always use AMD/NVIDIA video cards. These will significantly speed up the brute-forcing process.
We use a program with flexible settings to check a range of values very quickly in order to recover TrueCrypt passwords.
This is Passcovery Suite, which is a program that provides:
- scripts to search for passwords
- filter mask to create passwords according to a set of rules
- ability to change passwords using connected dictionaries
- support for AMD/NVIDIA video cards
Let's start.
Step 1: Launch Passcovery Suite and select the file with the data dump from the TrueCrypt disk
Here everything is as you would expect: choose the distribution (version for Windows x86/x64), install and run the program.
Choose the right TrueCrypt volume or file with data from the encrypted disk (accessible via the menu/toolbar or using the shortcut keys "Ctrl + O"):
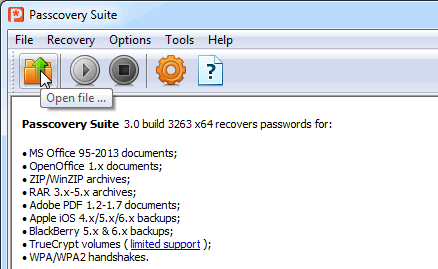
Here it is 1.bin for the data dump file from the logical disk and 64.bin for the file from the physical disk.
Step 2: Confirm that you selected the file to recover the TrueCrypt password.
Insofar as the data dump does not contain a clear structure, Passcovery Suite will make the assumption that this is TrueCrypt data. Agree and continue:
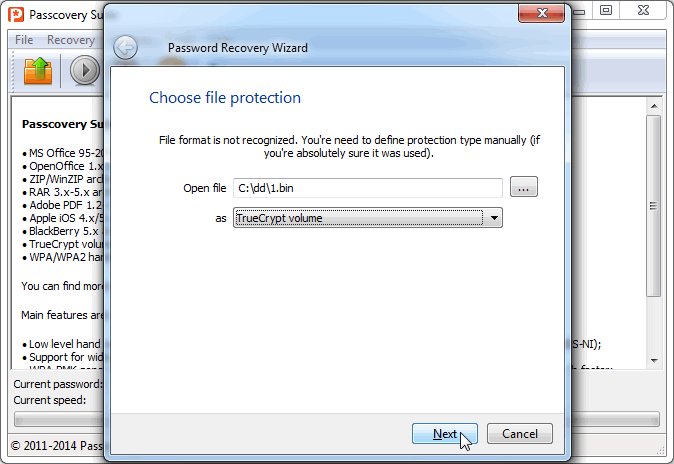
Step 3 - Define the hash function and the encryption algorithm to verify the passwords
Data in TrueCrypt are protected using algorithmic pair hashing and encryption. One of three hashing algorithms is set when creating the volume or disk:
- RIPEMD-160
- SHA-512
- Whirlpool
along with one of the encryption algorithms (encryption algorithms may be combined):
- AES
- Serpent
- Twofish
Now we need to choose which hashing-encryption pair should be checked.
Passcovery Suite supports all options, but it is impossible to know which pair is used for data protection, and it requires additional time to check each combination.
If there is no reliable information about the hashing-encryption pair, then select all options. This requires spending additional time, but only a full check guarantees that we will not miss the right password due to an error in pair selection.
Settings for various types of encrypted disks:
- encrypted logical disk (it is also appropriate for TrueCrypt volumes). Any hashing-encryption functions are possible:
![Recovering TrueCrypt password. Selecting a hashing-encryption pair]()
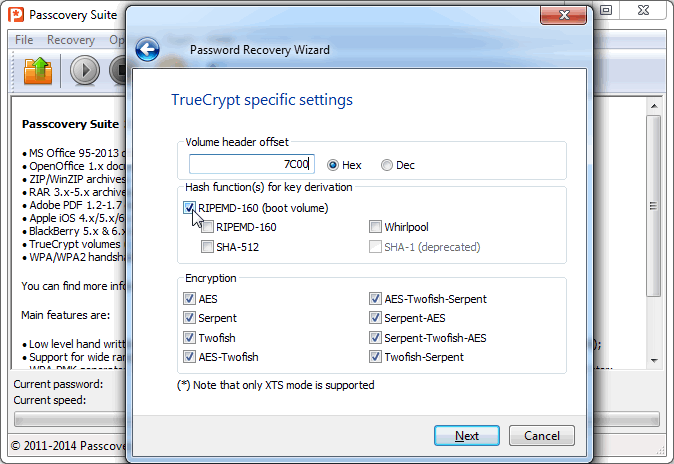
- encrypted physical disk. This disk contains the TrueCrypt bootloader, which makes its own adjustments:
![Recovering TrueCrypt password. Settings for a completely encrypted disk]()
- You must specify the address offset (7C00) to access the last 512 bytes of data, which are read at the first stage in the 64.bin file.
- Only one hashing option - RIPEMD-160 (boot volume) - is available.
Step 4 - Choose the password attack and configure its options.
Passcovery Suite will offer three types of attacks with a large set of options:
- brute-force attack. An attack that attempts all possible options. You can specify a character set, password length and install a simple mask. The slowest option
- brute-force attack with mask positioning. An attack that is attempted using only options that match the mask rules. You can set values individually for each password position (e.g., the first character should only be a number, the rest should be letters, and the last three are special characters) and set the length of the password. This is the best option when you know the password structure.
- dictionary attack. An attack that attempts all words in the dictionary. You can combine words from different Unicode-dictionaries, change, delete, rearrange, and replace characters. This is a great option for passwords that are formed by attempting common words.
Click here for more information about the capabilities of attacks. Video clips demonstrating these attacks can be found on our YouTube channel.
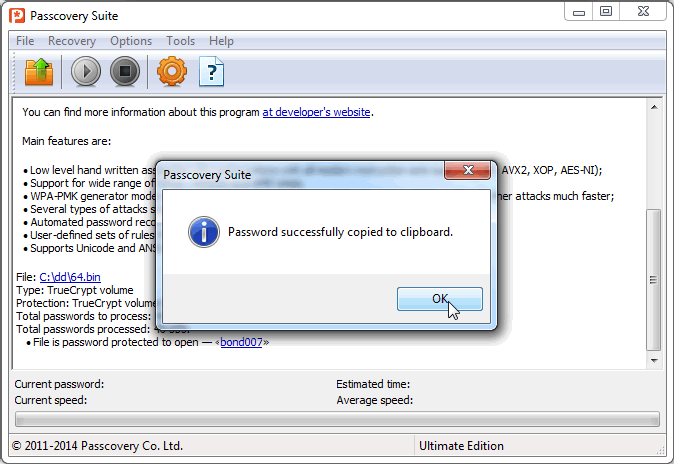
Step 5: Starting the TrueCrypt password recovery process.
When the settings are configured, we launch the search and wait for a result. When it is running, the Passcovery Suite saves the attack settings and status messages in a file with the extension .prs (Password Recovery Status). This means that we can always abort the attack and return to it later.
When the password is discovered, the program displays it as a hyperlink. Click on it, copy it to the clipboard, and you will be able to open the encrypted TrueCrypt disk:
Summary
Recovering TrueCrypt passwords is a thorny path that is covered in bitter disappointments and requires enormous amounts of time for searching.
If you do decide to attempt to recover a TrueCrypt password, then you will need to know something about the password structure. You will also need:
- 512 bytes of data
- several good video cards (NVIDIA Maxwell is the best)
- a program that will squeeze the maximum out of your GPUs
You have learned from these instructions how to obtain these data and what to do with them.