How to Recover a RAR Password If Only Half Is Readable
Here’s a question posted at reddit HowToHack. A user is wondering how to crack his RAR file. And do it fast, with GPU acceleration and enabled attack settings. The problem is a few characters of his long password got accidentally blurred and turned out totally illegible.

The problem is challenging enough for Passcovery programs and extended mask. Here’s how you can solve the riddle using Passcovery tools (and of course what works for RAR works for other formats as well).
Step-by-step solution
1. Start Accent RAR Password Recovery (or other required Passcovery tool) and open a password-protected archive (use the toolbar icon, the menu «File->Open» or the hotkey Ctrl+O – nothing unusual here).
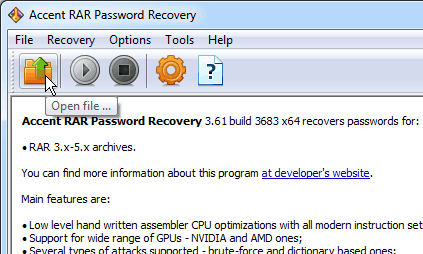
2. Read the file description (protection method), then choose the PPMd blocks scanning pattern and go to the attack selection step. Select “Brute-force with extended mask”.
3. Follow these rules to complete mask settings.
Let’s take the photo above as an example.
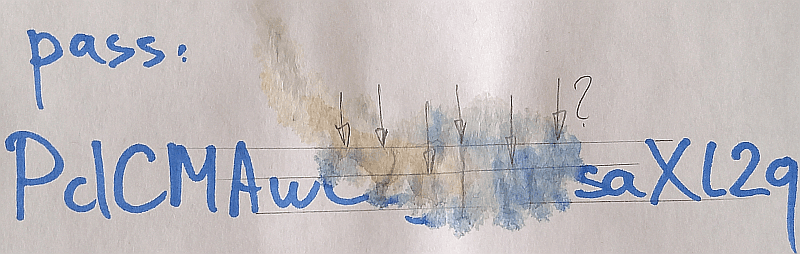
Only a part of the characters are clear while the rest have been washed away by latte (let’s mark the unknown characters with asterisk «*»): PdCMAw******saXl2q
Traces of damaged characters left on the paper (fragments of lines, distance and position of dots and stains etc.) allow us to make assumptions which might help reduce the number of verifications:
- first * - a capital letter, most likely “С”
- second * - a “high zigzag”, most likely “Z” or “2”
- third * - a lower-case letter with downward directed “tail”, most likely “g” or “y”
- fourth * - a “narrow” character with an element on top, most likely “1”, “7”, “T”, however “I”, “J”, “L” are also likely
- fifth * - a lowercase letter, really hard to guess which one, but for sure it is not a “narrow” one and it’s got no “tail”
- sixth * - a “high” and “thin-shaped” character, most likely “1”, “l”, “t”
Based on these assumptions we can specify sets of characters and define the mask as: PdCMAwC?0?1?2?3?4saXl2q
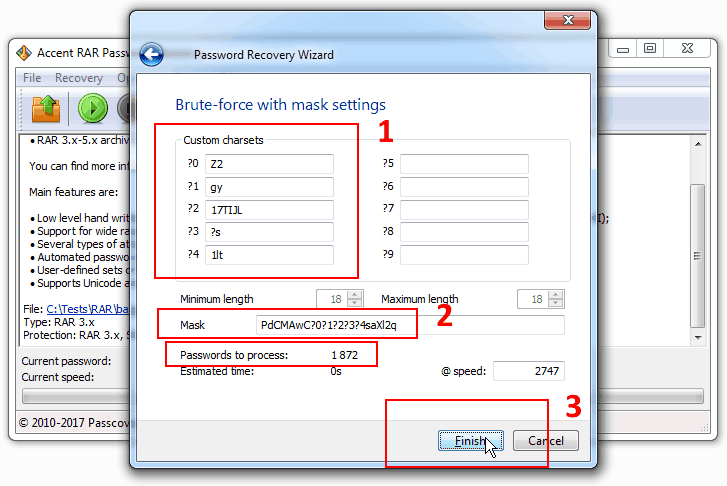
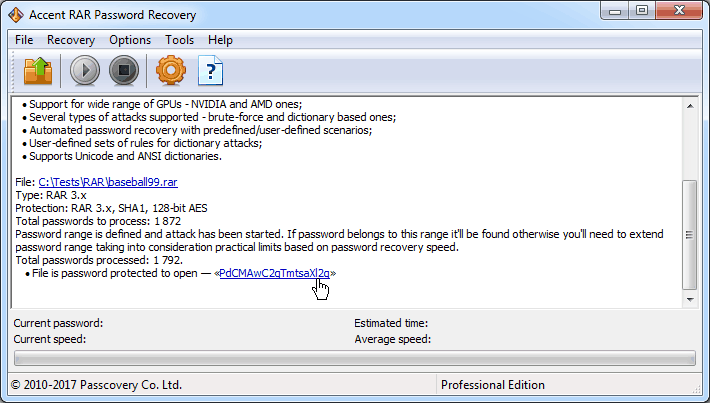
4. Start the search. With the assumptions made we’re down to only 1872 combinations to be validated. It is a piece of cake for any computer.
You may as well describe the fifth character in the mask using macro ?s (PdCMAwC?0?1?2?s?4saXl2q). But in this case you would not be able to define your own set of letters to be checked. You do remember that the “fifth * is a large-shaped letter without any tails”, don’t you? That means we could omit even more unnecessary checks by cutting down on thin-shaped characters and those with tails:
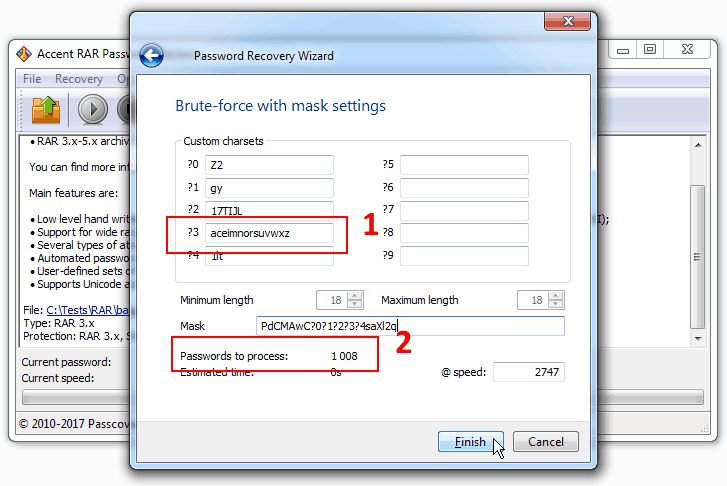
With extended mask you can define a list of possible characters for each position in the generated password which makes the mask a perfect tool to customize verification range with. By cutting off redundant validations you’ll be getting to the successful result way faster.
We recommend to start with the roughest assumptions (as we did in the example above) that is with the minimum number of combinations. Should the assumptions turn out wrong and you fail to find the password in the range of scanned combinations then you’ll just need to extend your view of the invisible characters — expand the range of verification and retry the search.
Why use extended mask?
It is true that there is an ordinary mask option in Passcovery programs apart from the extended one. You can use that one too. But it is not really useful when there is at least some information known about the password.
In the usual mask an unknown character is described with a symbol and verification of all the characters involves scanning of the entire specified range. Because of the drastic increase in the number of combinations to be checked it’s sure gonna take ages to complete the search.
Here’s what the usual mask would look like in our case:
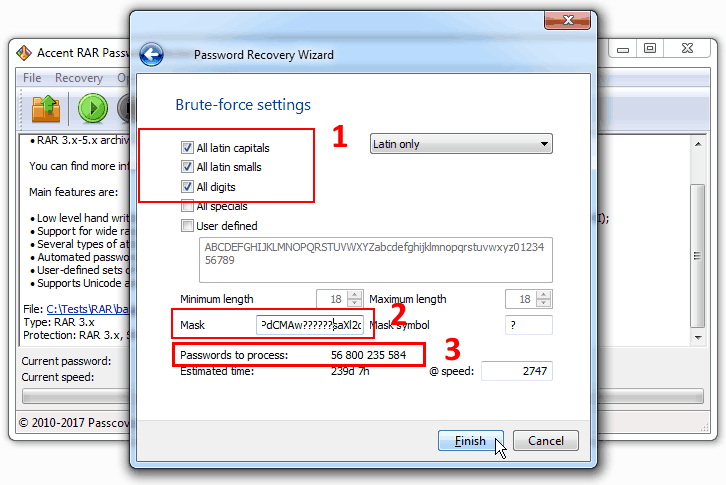
That is all possible combinations for the six unknown characters with a set of digits, small and capital letters will be checked which gives us 56,800,235,584 instead of 1872 combinations. See the difference?
So if you have at least some precise information about the password, try to use extended mask.
One more thing: the extended mask described above is also applicable in other Passcovery programs. The inherent algorithm is supported by all our applications.