Extended (positional) mask attack in Passcovery solutions
Successful recovery of a strong password is determined by the high speed of attack and effective management of range settings.
Passcovery programs with finely tuned speed parameters show excellent results both on CPU and NVIDIA/AMD graphics cards. Try them out! The demo versions with no speed limitation are available at no charge.
All our programs offer a few options to manage the range settings:
- Dictionary attack with password mutation — enables to customize password mutation (variation) rules and to join up to four dictionaries
- Mask attack — enables to specify the known part of your password
- Extended mask attack — enables to define variation rules for each symbol individually
Extended (positional) mask attack is a flexible and powerful tool that enables to cut down on unnecessary checks. The option allows you to define a range of characters to be used in each position of the password when it is generated, and omit the unnecessary ones. That helps reduce the number of possible combinations and saves time.
If you are recovering a strong protection password and you know something about its structure then «Brute-force with extended mask» would be the perfect method to use.
Review the examples to see how it works and what it’s all about.
Using extended mask
The extended mask option is available in all Passcovery programs. The examples below illustrate the use of AccentPPR as a password cracker for all versions of Adobe PDF; the same scenarios can be fulfilled using any other Passcovery program.
Start the required Passcovery program and open your password-protected file (Menu File → Open or click on the toolbar icon):
Fig. 1. Opening a password-protected file
Read the general file description (file format, protection method etc.) and go to the attack selection step:
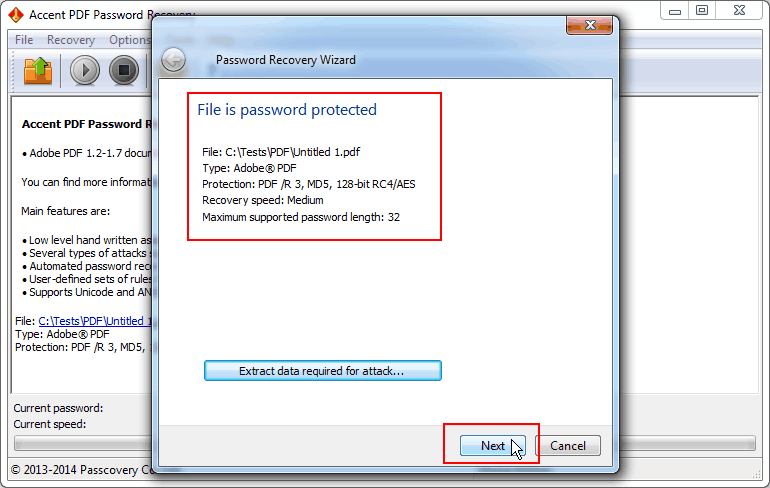
Fig. 2. File protection data
Select «Brute-force with extended mask», complete mask settings and start the search:
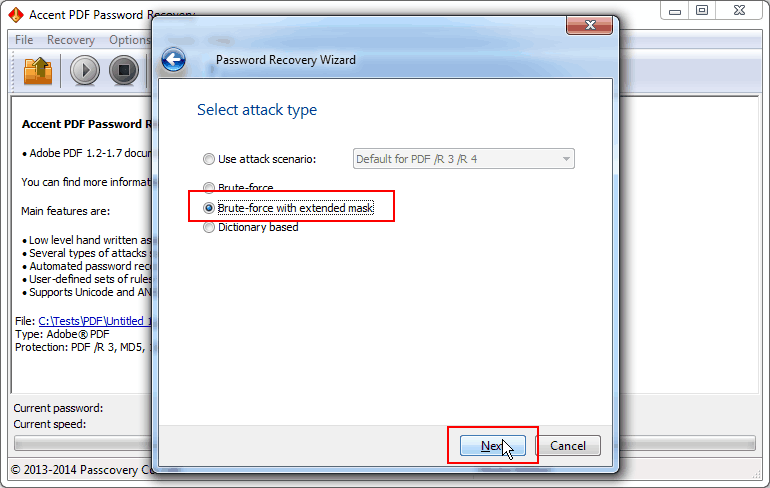
Fig. 3. Password attack selection
To customize the password generation process you can specify up to 10 sets of characters for each position of the mask. A mask is defined using simple prefixes. You can limit the length of your mask if necessary. Find more details in the help file.
Example 1. Mask for a password of 6 digits, one letter (Latin lowercase) and one special character
In the case the sets of digits/letters/special characters are tried in full without abbreviations then the corresponding mask will look like this: ?d?d?d?d?d?d?s?e
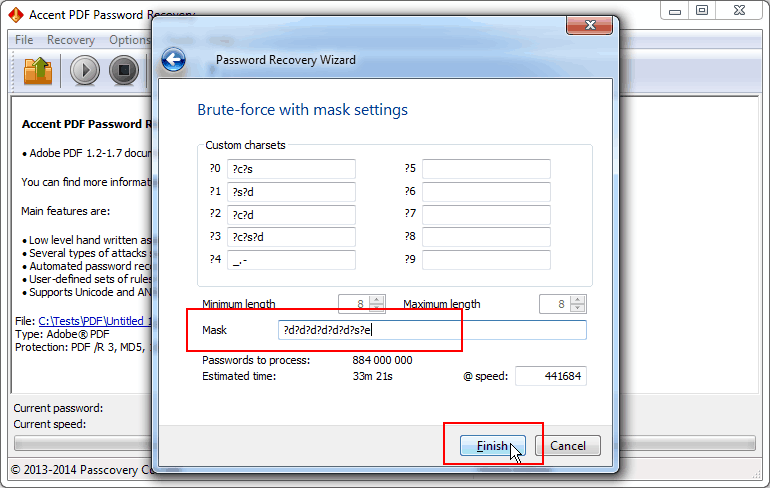
Fig. 4. Mask with full sets of characters
In the case you need to reduce a set of characters (for example include only the digits «123456» and use only these special characters «=+!») then you have to customize these sets of values (that is sets ?0 and ?1), and then use these ranges in the mask to generate the passwords: ?0?0?0?0?0?0?s?1
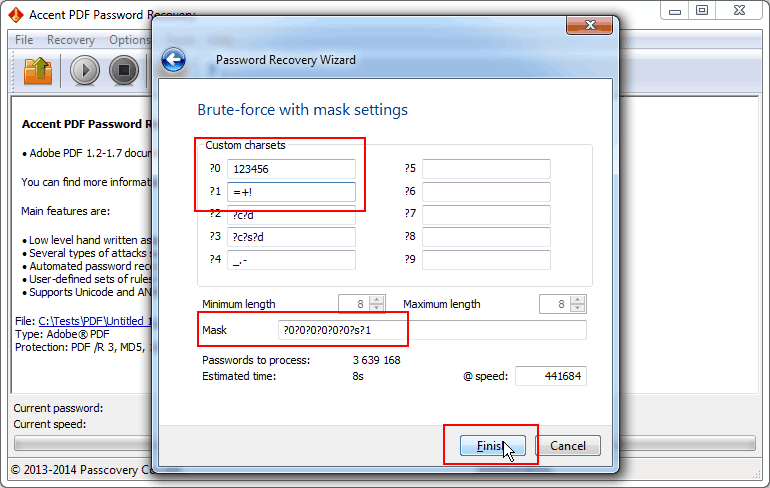
Fig. 4. Mask with reduced sets of characters
Example 2. Here is an example of a mask for a password with known structure and characters (PDL description: [gG] [oO0] [oO0] [dD] [\. \0] [tT] [iI1] [mM] [eE3])
It is now required, as follows from PDL description, to specify the needed sets of characters and define the mask using special prefixes: ?0?1?1?2*3?4?5?6?7
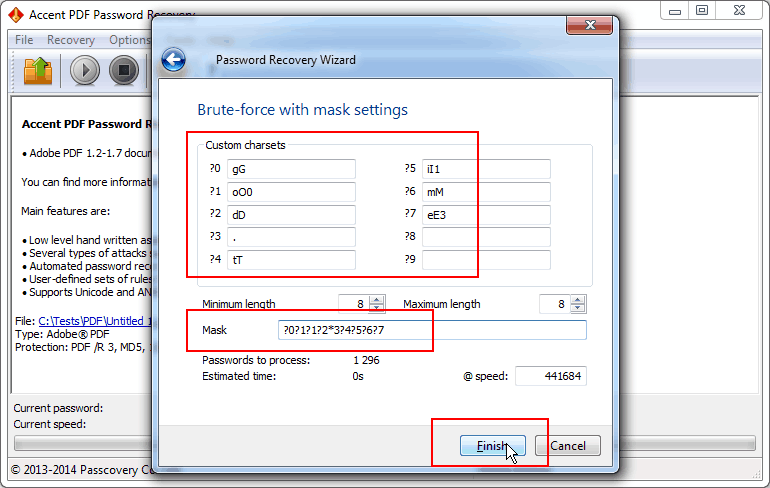
Fig. 5. Mask for a password with known structure and characters
Example 3. A mask for a variable-length password, with a capital letter at the beginning, letters in the middle and a digit at the end
That’s a simple case. The mask will look like this: ?c*0?d
The first and last position of the password will be a capital letter and a digit respectively. The prefix *(asterisk) will tell the program to use the characters from the #0 set (those are uppercase and lowercase letters shown in the screenshot) for all other positions in the password. The number of positions will vary based on the varying length of the password.
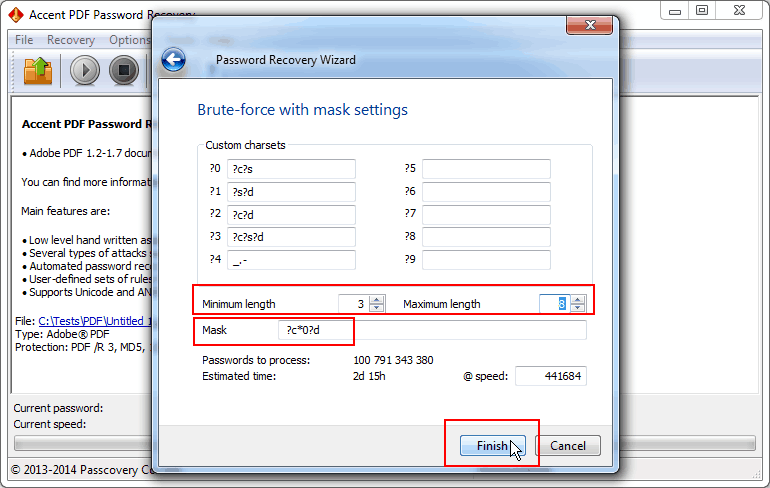
Fig. 5. Mask for a variable-length password
Example 4. You know how your password begins but the end part - the characters and length - totally slipped your mind
In that case your extended mask would look like this: 12805233?0*s
First goes the known part of your password (12805233). Then you describe the unknown part using the charset “?0”, which denotes all printable characters — macro “?a”. By setting the minimum and maximum length you define the number of characters in the end part of your password within the specified range.
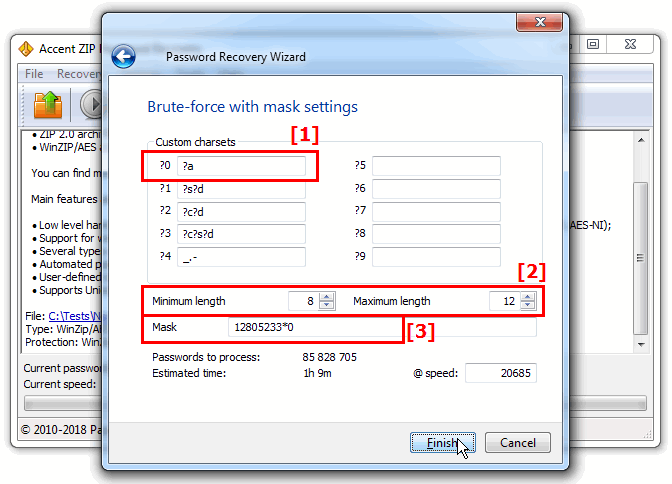
Fig. 1 Mask attack when the length of the password’s tail end is unknown
Passcovery solutions for password recovery
We offer a universal all-in-one solution for a large number of popular formats and a dedicated line of programs for specific file formats.
All the programs have a unified interface featuring the same finely tuned speed parameters. Our solutions offer acceleration on AMD/NVIDIA GPUs.
Trial editions for Windows x32/x64 are available for download.
| Passcovery Suite for Microsoft Office, OpenOffice, Zip, Rar, TrueCrypt, Apple iOS, BlackBerry OS, WPA/WPA2 |
Download x86 (18912 Kb) |
Download x64 (21172 Kb) |
| Accent OFFICE Password Recovery for Microsoft Office/OpenOffice |
Download x86 (10116 Kb) |
Download x64 (11688 Kb) |
| Accent PDF Password Recovery for Adobe PDF |
Download x86 (7208 Kb) |
Download x64 (8232 Kb) |
| Accent RAR Password Recovery for RAR3/RSR5 archives |
Download x86 (13420 Kb) |
Download x64 (14440 Kb) |
| Accent ZIP Password Recovery for Zip archives with classic and WinZip AES encryption |
Download x86 (7748 Kb) |
Download x64 (9136 Kb) |
Should you have any problem setting an extended mask please feel free to contact our helpdesk. We will help you and add an example to this page based on your case.