Will Passcovery Crack My DOCX? Let's See
DOCX file passwords can be cracked, but there are no guarantees. Unlike old Word 97-2003 DOC files, which can be decrypted without a password by finding the encryption key, DOCX requires sequential brute-force testing. Neither our software nor any other can bypass this limitation.
The goal of any good software: intelligently narrow the search space and test it quickly. Our programs offer advanced mask patterns, dictionary mutation, and AMD/NVIDIA/Intel Arc GPU support (for speeds tens of times faster than CPU).
We don't guarantee successful recovery, but we guarantee maximum search speed on your hardware.

What Determines DOCX Cracking Success?
Three factors work against you:
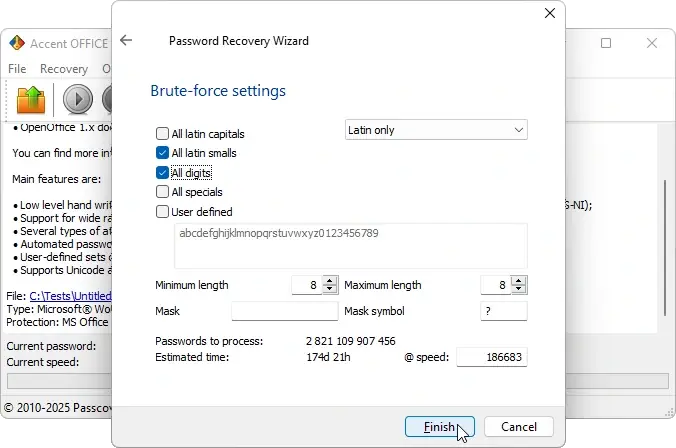
Password complexity. Entropy (number of possibilities) grows exponentially:
password_charsetpassword_length
A password with letters and digits (62 characters) that's 6 characters long: 626 = 56 billion combinations. Add two
more characters, and it becomes 628 = 218 trillion. The difference between "we'll crack it in a week" and "forget it" (even for Word 2007).
Word version. Word 2024 checks 14 times slower than Word 2007. Microsoft strengthened the hashing algorithm and key derivation (from 50,000 to 100,000 iterations).
Your hardware. Without a GPU, even simple brute-force attacks can take weeks, months, or years. With a modern graphics card, you can reduce that to days or hours.
How Long Will Cracking Take?
Honest estimate: from seconds for simple passwords to centuries for complex ones. On a mid-range GPU (RTX 4060), a 6-character password with lowercase letters and digits takes 3 hours with full brute force for Word 2007. For 8 random characters – that's already 175 days.
The good news is that most passwords aren't random. We use patterns, familiar words, dates, names. We're lazy! And that's when masks or dictionary mutations reduce search time by hundreds of times. A seemingly strong password like "P@ssword2024" can be found in minutes, not years.
Why can't we give an exact forecast? The correct password could be the first on the list (your lucky day) or the last (your nightmare). The table shows COMPLETE brute-force time (but remember – with a good mask, real timeframes will be shorter).
| Password Type | Combinations at 6 characters | Cracking time on RTX 4060 | Combinations at 8 characters | Cracking time on RTX 4060 |
|---|---|---|---|---|
| Digits only | 1,000,000 | ~5 seconds | 100,000,000 | ~9 minutes |
| Letters a-z | 308,915,776 | 27 minutes | 208,827,064,576 | ~12 days |
| Letters + digits | 2,176,782,336 | ~3 hours | 2,821,109,907,456 | ~175 days |
| Full set (96 characters) | 782,757,789,696 | ~48 days | 7,213,895,789,838,336 | ~1,225 years |
| *Tested on NVIDIA GeForce RTX 4060 in Accent OFFICE Password Recovery, 186,683 passwords per second | ||||
Three Strategies to Speed Up Cracking
Instead of blindly testing all combinations, use methods to narrow the range:
Advanced mask – when you remember parts or the structure of the password. Started with a capital letter, ended with a couple digits?
Mask ?c*s?d?d reduces 218 trillion to 31 billion combinations (7,000+ times fewer). Know the beginning
"Qwer"? Mask Qwer*0 leaves 7 million combinations – checked in minutes.
Positional mask examples
Dictionary mutation – accounts for human behavior. Load a dictionary, set transformation rules (a→@, o→0, add year, capitalize first letter), the software generates millions of variations tailored to your case. The word "password" becomes P@ssw0rd, Password2024!, pa$$word, and only your specified combinations are checked. Dictionary mutation example
GPU acceleration – tens of times faster (depends on CPU and GPU). A graphics card checks thousands of variants in parallel on thousands of compute cores, while a CPU does the same work on just a few. AMD Radeon RX 9070 XT delivers 25,000 passwords/sec for Word 2024, NVIDIA GeForce RTX 5090 – up to 77,000. Intel Core i5-12400F CPU – only 540 passwords per second. The GPU advantage is obvious!
The right combination of methods reduces DOCX password search time from years to hours.
Expert Tip: Password Psychology
According to our statistics, up to 40% of office passwords follow predictable patterns:
- Word + year (Password2024, Summer2023)
- Name + date (Anna1985, John0312)
- Simple substitutions (P@ssw0rd, M1cr0s0ft)
- Keyboard combinations (Qwerty123, Asdf!234)
Special characters usually appear at the end, not in the middle – use this for your mask. Always start with dictionary mutation: there's a chance to find the password in minutes instead of days.
GPU Performance: What to Choose?
For one-time recovery, whatever you have is enough – even a GTX 1660 delivers 7,000 passwords/sec for Word 2024, which is 13 times faster than an i5-12400F CPU.
For regular tasks, the optimal choice is top-tier gaming cards from previous generations: prices have cooled down, yet performance for password cracking remains excellent. Current-gen flagship GPUs show the best performance but typically have worse performance-per-dollar due to high cost. Their purchase is justified only for constant security auditing.
For Word 2007-2010, speed will be 3-4 times higher on the same hardware.
To choose the optimal graphics card for your tasks and budget, check out our GPU ranking for password recovery.
DOCX vs DOC: Why the New Format Is Harder
The DOC format (Word 97-2003) uses a 40-bit encryption key. That's only 1.1 trillion key possibilities (the formula is similar to password combination calculations: 240). You can brute-force all keys in a few hours or use rainbow tables: the key is found, the file decrypts and opens, though the password remains unknown.
The DOCX format uses AES-128/256 with a 128-256 bit key – brute-forcing all keys is impossible even over billions of years (2128 or 2256 is no joke). The only way is to find the password itself through brute-force.
More details on methods for different versions: How to open an encrypted Word file by Office version.
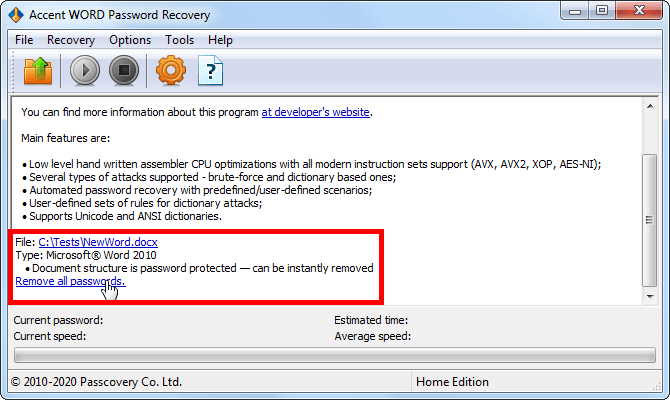
Simple Protection: Instant Removal
If a DOCX is protected not by "Password to open," but by editing restrictions, VBA password, or "Password to modify" – protection is removed instantly regardless of complexity and Word version. In all these cases, the file uses not data encryption, but a simple flag, protection from accidental changes. If Word opens the file but limits actions within it, password brute-forcing isn't needed.
What Do Passcovery Programs Guarantee?
We guarantee:
- Maximum speed on your hardware (ASM optimization, NVIDIA, AMD, Intel GPUs)
- Flexible tools: advanced mask, dictionary mutation, attack scenarios
- Support for all Word versions 6-2024 (Microsoft 365), DOC and DOCX formats
- Demo version works at full speed – test before you buy
We DON'T guarantee:
- Success for passwords longer than 6 random characters
- Specific timeframes – depends on password position in the variant list
Honest positioning: we provide the best tool, not a magic wand. We'll find "Password123" in minutes. "aB3!xK9zQ2" – chances are minimal.
So Will We Crack the DOCX or Not?
Yes – if you give the software something to work with. Remember the password structure? A mask reduces trillions of checks to millions. Suspect a dictionary word with substitutions? Mutation will check thousands of appropriate variations in seconds.
Passcovery programs deliver up to 77,000 passwords/sec for Microsoft Word 2024 on top-tier GPUs. But speed without direction is blind brute-force. The formula for DOCX cracking success: your memory + our algorithms.
Passcovery Programs for Microsoft Word
Download and install demo versions – they'll show realistic forecasts for your file.
Accent OFFICE Password Recovery
for Microsoft Office 6-2024, Microsoft 365, OpenOffice
Passcovery Suite
for Microsoft Office/OpenOffice, Adobe PDF, RAR, Zip, Apple iOS backups, TrueCrypt, WPA/WPA2 handshakes
Frequently Asked Questions
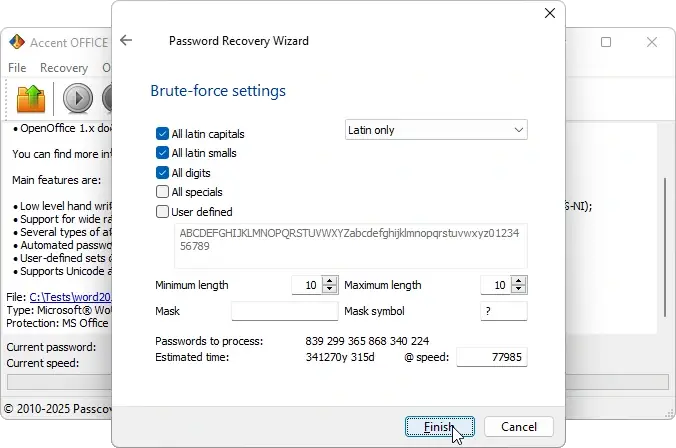
No, cracking a DOCX with a truly random password of 7+ characters is practically impossible in reasonable time, even on powerful graphics cards.
For a 10-character random password from 62 characters, that's 6210 ≈ 8.3×1017 combinations. On NVIDIA RTX 5090 (~77,000 passwords/sec), that's about 341,000 years of continuous brute-forcing. Even 1,000 such GPUs would only reduce the time to 341 years.
But most passwords aren't random. A password like MyDog2015!! can be found in minutes with dictionary attacks, while xK3!mQ9z@L2v – practically never.
The cost consists of software price ($50–500) and, if needed, a graphics card ($300–2,000). Online services charge $20–100 but don't guarantee success for complex passwords.
For simple passwords, affordable software and a regular PC are sufficient. For complex ones – professional software and a powerful GPU are required, which is justified for regular tasks or corporate use.
Alternative – specialized company services ($100–300 per file), but they also don't guarantee cracking complex passwords.
A random password of 10+ characters with mixed case, digits, and special characters is securely protected against modern cracking methods.
DOCX uses strong AES-256 encryption with 100,000 iterations of SHA-512 . The weak link is the password itself. Avoid:
- Dictionary words
- Dates and simple numbers
- Obvious combinations
- Letter-to-number substitutions
Good password: mK9$vL2@xR7!
Bad password: MyPassword2026!
The demo doesn't limit cracking speed and uses the same code as the full version. The only limitation is in displaying results – only the first 2 characters of the password are shown.
We at Passcovery do this intentionally. It allows you to honestly evaluate performance on your hardware. Buying a license doesn't speed up cracking – only a more powerful GPU does that.
Rethink your strategy: use masks, dictionaries with mutation, and check the protection type.
- Check protection type – it might be an editing restriction that's removed instantly.
- Use a mask – knowing the password structure reduces brute-force by hundreds of times.
- Dictionaries with mutation – names, dates, company names.
- Assess reality – a random 10+ character password could take years to crack.
Microsoft Word 2024 (starting with Word 2013) uses more iterations of the key derivation hash function, making brute-force up to 20 times slower than Word 2007.
Example: a 6-character password (lowercase+digits) on NVIDIA RTX 5090 – ~30 minutes for Word 2007 and ~8 hours for Word 2024.
Online services are effective only for simple passwords. For complex passwords, you need local software with GPU acceleration.
Typically, services allocate 10–30 minutes of computing time – not enough to brute-force complex combinations.
Exception – old DOC files (Word 97–2003), which are decrypted using rainbow tables, for example on AccessBack.com.