Brute Force Attack is Faster Than a Dictionary Attack. When and Why?
The user wrote: «I crack ZIP the password in your Passcovery Suite program. Excellent speed of search at attack of a brute force! But it strongly gives at attack according to the dictionary. In what the reason?»

The reason in speed of breaking of ZIP archives with classical encryption.
A dictionary attack will be slower than a brute force attack for formats at high speed of recovery of passwords. The matter is that reading and preparation of passwords from the file of the dictionary demands much more time, than validation of passwords.
That is, at attack of a brute force, passwords to Zip to archives with classical enciphering can get over with a speed in some billion passwords a second (on the good videocard). And at the same time attack according to the dictionary will show only million passwords a second. And when using governed speed drops even lower…
For formats at low speed of restoration (and now it honor all formats) a difference in speed between attack according to the dictionary and attack of a brute force it will not be appreciable as validation of passwords takes more time, than reading/preparation of passwords from the dictionary file.
Formats where attack according to the dictionary will be more slowly, than attack of a brute force:
- Zip-archives with classical encryption
- Microsoft Office 97-2003 documents
Formats where speed of attack according to the dictionary will be same as at attack of a brute force:
- Zip archives with WinZip AES enciphering
- RAR3/RAR5 archives
- OpenOffice, Microsoft Office 2007-2016, Adobe PDF documents
- TrueCrypt volumes
- Apple iOS/BlackBerry OS backups
- WPA/WPA2 handshakes
About types of password attacks
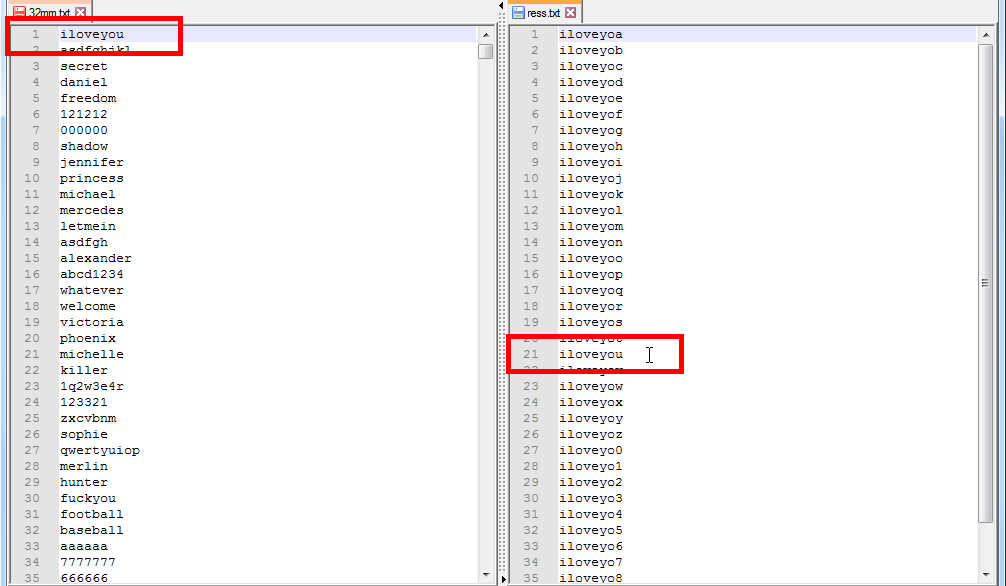
Dictionary attack. Passwords are read out from the dictionary file - the usual text file where it is row-wise words passwords are written down. The program for recovery of passwords consistently reads out these words passwords and checks them.
Brute force attack (direct search). Passwords are generated by the program for password recovery from the set of symbols specified by the user and checked right then. Optionally attack of a brute force can use a password mask - a template for creation of passwords.
Passcovery Suite for password recovery
Passcovery Suite restores passwords for files of popular formats. Provides acceleration of search of passwords on the videocards AMD/NVIDIA. Offers enhanced features for carrying out attack according to the dictionary and attacks of a brute force: work scenarios, mutation of the dictionaries, expanded mask. The program restores/deletes a number of passwords instantly.
The demo version for Windows x86/x64 is available on the Passcovery website:
| Passcovery Suite for Microsoft Office, OpenOffice/LibreOffice, Adobe PDF, Zip, RAR, TrueCrypt, Apple iOS, BlackBerry OS, WPA |
22.01 | Download x86 (16420 Kb) |
Download x64 (18996 Kb) |
|
| ||||
For recovery of passwords to Zip archives, Passcovery also offers a separate product:
| Accent ZIP Password Recovery for Zip archives with classical and WinZip AES encryption |
22.01 | Download x86 (7452 Kb) |
Download x64 (8956 Kb) |
|
| ||||
Three burning questions about password attacks
It lies in the searching range and searching time: in the case of brute force attack the range is not defined and can be infinite, whereas for a dictionary attack it is limited to the number of entries of a dictionary.
In both cases, the principle of attacking is the same: testing words and phrases trying to guess the password. The difference lies in the number of possible passwords to be tried.
In the case of brute force attack, the range is predefined beforehand and may have no limits. This is both the strong and weak point of the attack. It's great, of course, to be able to customize the range but it is sure to take ages to test an overly extensive range. Actually, you may as well keep trying till the end of your days and yet fail in the end 😁
Dictionary attack uses a preselected library of words stored in a dictionary file. There are various dictionaries: small, large and gigantic, thematic dictionaries, language dictionaries, dictionaries of popular passwords, leaked password databases etc. You can (and should) create your own dictionaries and enable mutations of your word lists. However the number of guesses will be finite.
It turns out that dictionary attack is likely to finish faster if the password is a word that is in the dictionary. Whereas brute force attack is more failproof as sooner or later you are bound to find the right password.
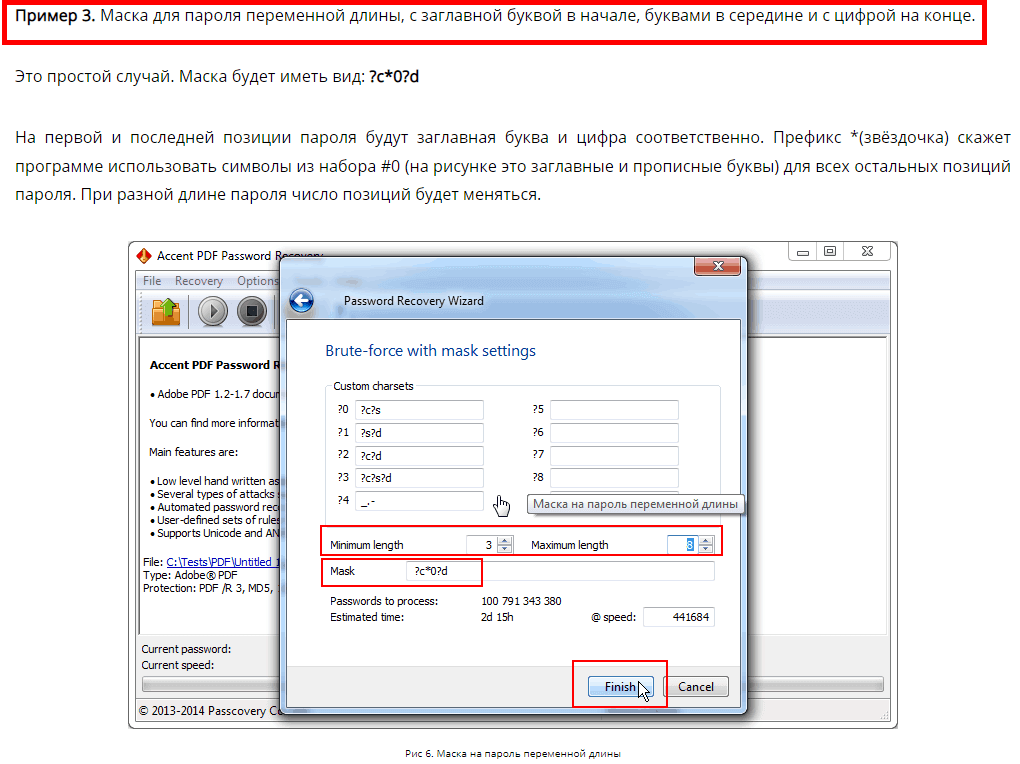
This is a type of brute force attack used when there's some information about the password - a known part or some characters.
A brute force attack involves exhaustive trying all passwords.
But when you know at least something about the password, it is recommended to set a mask i.e. a template for generating passwords. In that case you will only try passwords that comply with the mask. A mask attack enables cutting off mismatching combinations and save a lot of time recovering the password.
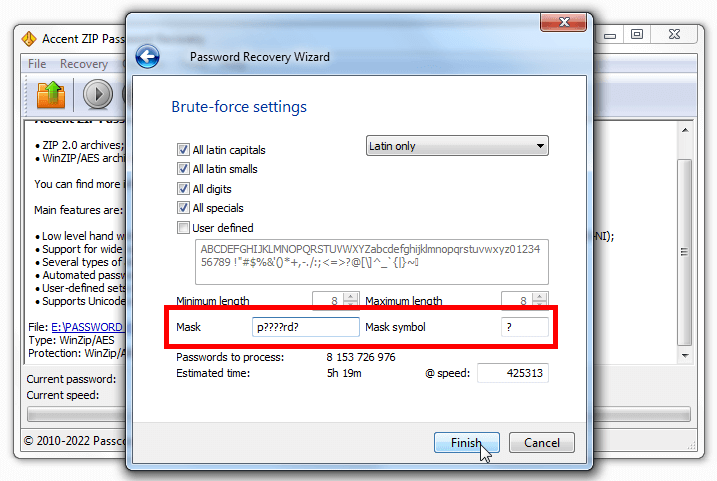
Unlike a simple mask when you can only define the known characters, an extended mask allows you to specify a set of likely characters individually for each position in the password.
Extended mask expands the arsenal of a brute force attack by cutting off unnecessary checks and concentrating the resources on the most probable passwords.
All Passcovery programs support the extended mask option. See examples of using the extended mask attack here.