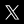Specifics of Cracking RAR Files With Graphics Cards
Here at Passcovery we compare different GPUs and present a ranking based on their password recovery performance.
Basically our ranking is an unbiased chart of the best GPUs to crack passwords with. However when it comes to RAR files a misfire may occur. Sometimes users with [fast] graphics cards may end up with this kind of freeze:
What is the problem, its effects and how to solve it – find all the answers in this article!
What is the problem, what does it entail, and how can it be fixed? Find the answers in this article and in the video breakdown on our YouTube channel.
The naughty nature of RAR
In regards to password cracking the RAR format is unpredictable. It is very different from all the other formats supported by our Passcovery Suite. Each RAR archive is unique and this uniqueness is due to the following:
- What is the version of archive - RAR3 or RAR5? (RAR5 is easier to crack)
- If it’s RAR3 then what about the headers – are they encrypted or not (encrypted ones are easier to process)
- If the headers are not encrypted, what compression method is used in the archive (from 0 to 5)
- If the compression method is “Stored” (0, no compression), what is the size of the archive itself?
All these factors affect the speed of password attack.
Effects of compression method and file size on the speed of RAR password cracking
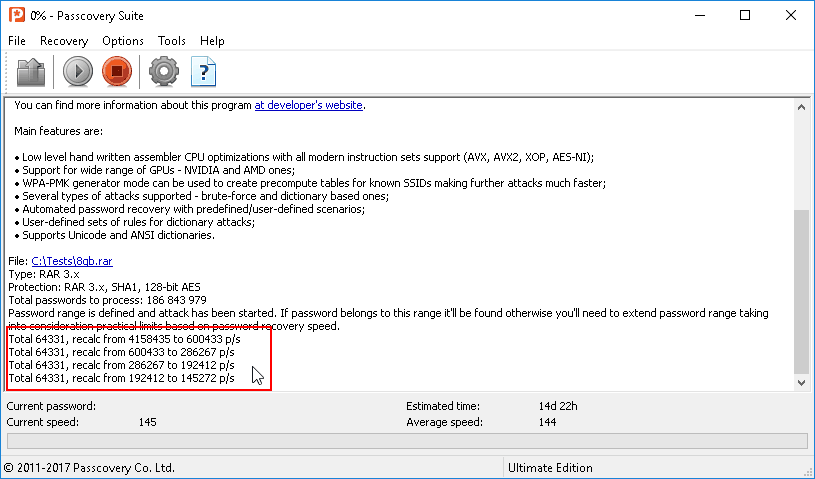
When creating a RAR file you can choose from the six compression methods available:
The biggest trouble is the “Store” option – a method without any compression (an archive is a container that stores files in their original size).
Let us why it’s a problem.
To validate a RAR file it is necessary to convert a password into a key and then decrypt something from the archive and check the result.
It’s great if the headers are encrypted. It would also be good if an archive was created with compression (any method other than the “Store” one). Then the key can be used to decrypt either the headers or just the initial part of the archive. It works fast (and even faster on graphics cards).
But if the headers are not encrypted and the compression method is “Store” you will have to decrypt the entire archive and compare its checksums with the reference ones.
And in this case the size of an archive is of great importance.
Do you remember how long it took to archive your huge file? Well, now the process is reverse. When testing each password from a given range the password cracker every time completely unpacks the archive.
That means the larger the archive, the more time it takes to validate the password.
GPU-enabled cracking of large RAR files
Recovery of RAR passwords on video cards is associated with one more specific feature – a GPU accelerates “password → key” conversion, but it does not accelerate validation of the key since it is always performed on CPU.
And that’s why you might get a freeze while processing a large RAR file.
Once GPU receives a pack of passwords to be further converted into encryption keys it quickly returns them to CPU and waits for the next pack of passwords to process. But CPU cannot generate it because it is busy validating a whole bunch of received encryption keys. Again and again it unpacks the archive sequentially verifying each key from the data pack.
CPU is loaded with the checking process while GPU is being idle in anticipation of the next task. And the password-cracker seems to be frozen…
A side effect of the situation is that the current status of password recovery is not saved until the current block of keys is fully validated. If it lasts, say, two hours and at some point the process stops then the data of all completed checks will be lost and the next time you run .prs-file the check of this block will start over again.
Solution to the Problem
There is none. If you are trying to crack a large RAR file and your program window looks like that in the screenshot at the beginning of this article, then your CPU is simply supercharged and stifled with a stream of encryption keys calculated on GPU, which leaves CPU no time to validate them.
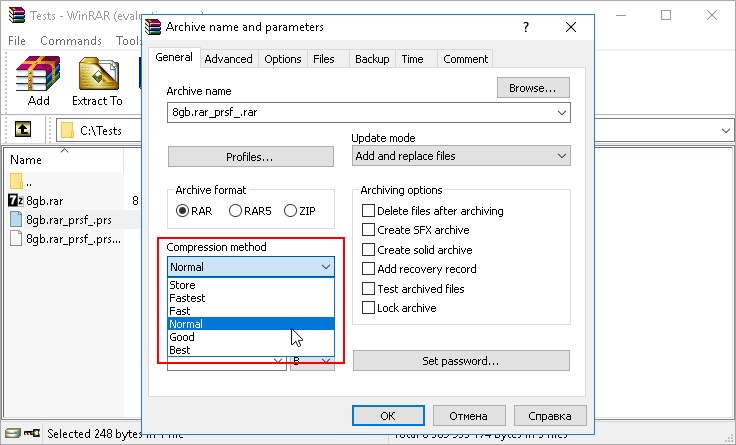
In this situation we recommend that you try to disable GPU (Menu Options → Preferences → GPU Configuration) and check the speed of password attack without GPU acceleration – that is with CPU only (in our demo versions the speed is unlimited).
In the case you see that the speed of password attack has [practically] not decreased then there is no point in using a graphics card to crack this archive. In this case an extra bonus that comes along with disabling GPU will be continuous recording of the password recovery status.
With different (simpler in structure) archives the situation will be different. In that case the GPU acceleration will very effective. Just make sure you enable it.
Passcovery solutions for RAR
We offer two software tools created to recover RAR passwords:
| Accent RAR Password Recovery for RAR3/RAR5 |
25.04 | Download x64 (10772 Kb) |
||
| Passcovery Suite for RAR; as well as Zip, Microsoft Office, OpenOffice, TrueCrypt, Apple iOS, BlackBerry OS, WPA/WPA2 |
25.04 | Download x64 (17896 Kb) |
||
The programs demonstrate excellent attacking speed and are equipped with perfect time saving options – validation range management tools:
- Dictionary attack with pre-set mutations (example #1, example #2)
- Extended mask attack (example #1, example #2)
Learn more and try out our RAR cracking solutions. Demos for Windows x32 / x64 are available on the Passcovery websites.
Three questions about RAR password recovery
RAR protection algorithms ensure super-strong encryption and protection of packaged and archived data.
When archiving a file the file owner sets a password using WinRAR, and the file content is encoded in accordance with the standards of reliable encryption i.e. using a 128/256 bit key, which makes a RAR file a citadel of great strength.
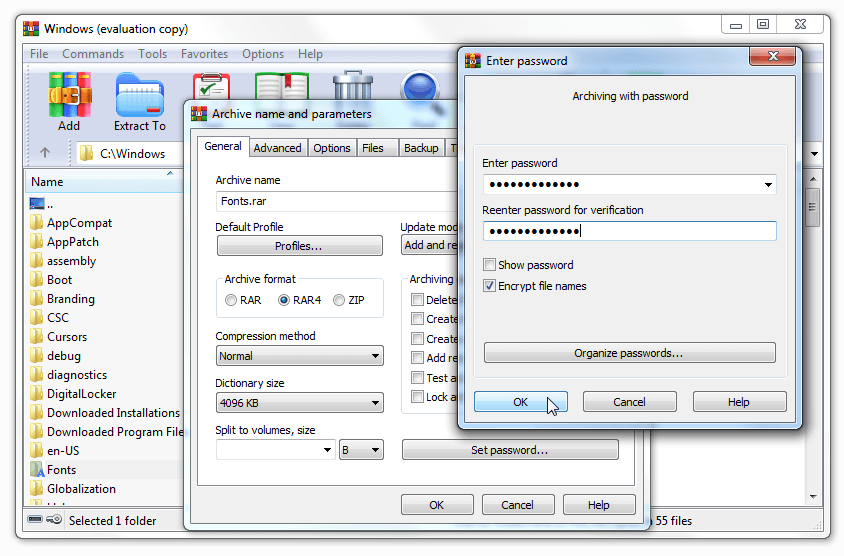
Once the password is set, it will only be possible to access data through entering the correct password. Everything is serious in WinRAR: there are no back doors, no room for vulnerability of algorithms or secret hacks. The data is securely packed and protected.
That's why people choose WinRAR 💗💗💗
Yes, but only if the password is simple or you know much about it.
Hacking a RAR password would require an exhaustive search through options until you discover the one correct combination. The speed of searching will depend on the size of an archive. The good thing is that GPU acceleration on NVIDIA, AMD and Intel Arc graphics cards is supported for RAR files.
Attacks on lost RAR password:
- Brute-force attack – exhaustive search through all possible combinations
- Extended mask attack – searching through a limited number of customized options
- dictionary attack with mutations – searching through ready-made and modified wordlists
It's a good idea to run a dictionary attack first. Perhaps your lost password will be among the most popular ones.
This is a program to recover lost RAR passwords.
The author of WinRAR informs that they do not supply any password cracking software and that there is a big number of "password cracking tools" supplied by independent developers.
The requirements for such tools are determined by the enhanced reliability of RAR password protection:
- full support of all versions of the format (including the PPMd algorithm 😜)
- variety of password attacks 💃
- flexibility of range manipulation options ⚡
- high-speed brute force attack 🚀
- acceleration on NVIDIA/AMD/Intel Arc graphics cards 💣
All these features are available in Accent RAR Password Recovery, the recommended RAR password unlocker.
Disclaimer: Disclaimer: The information on this page is for educational purposes only. The methods and examples described are intended solely for the purpose of recovering access to your own files and passwords. Any other use may be illegal.